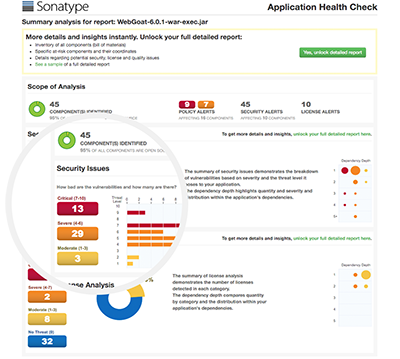
Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Descrição
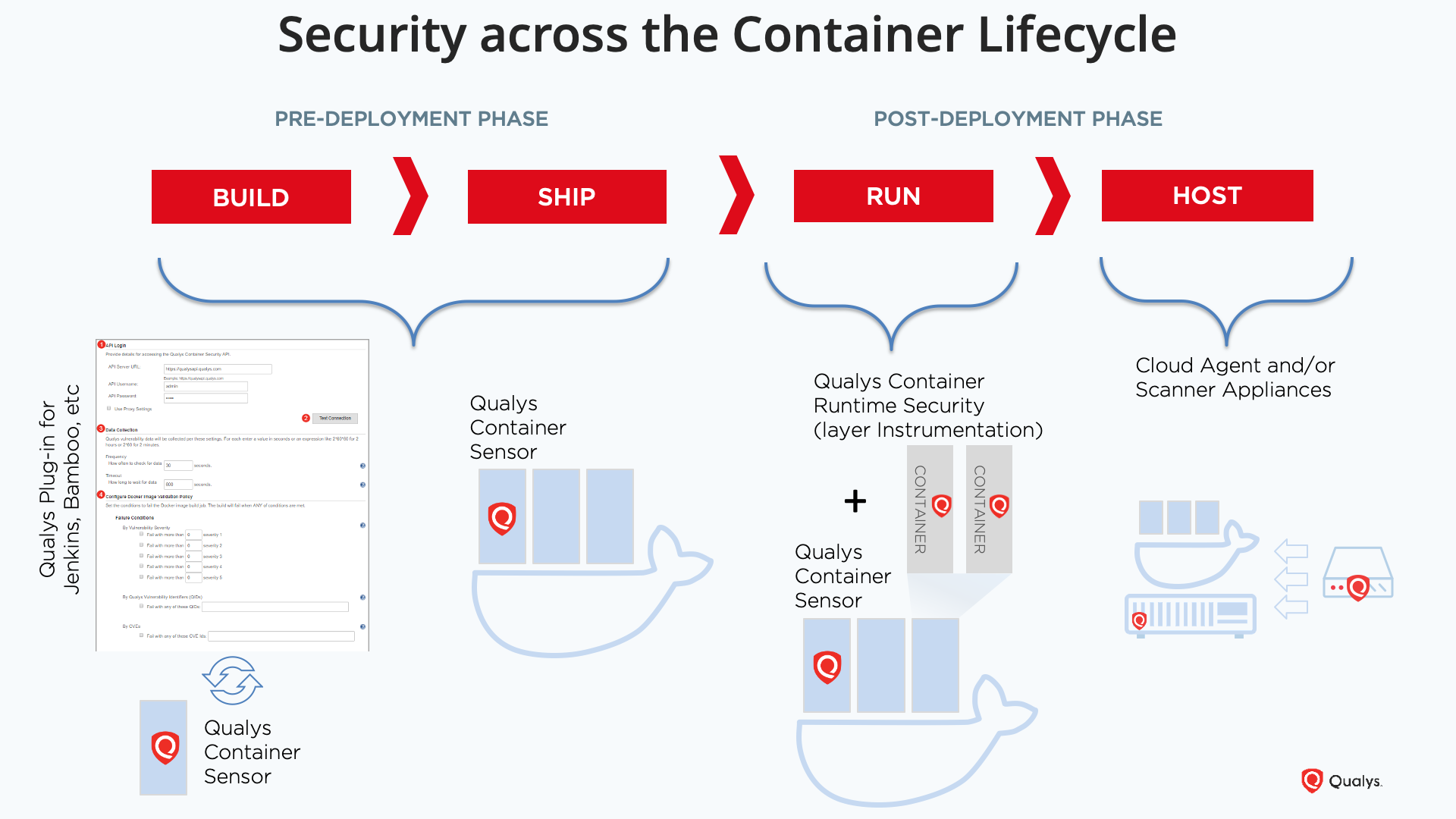
Add Ergonomic Security to Your CI/CD Pipeline
CI/CD Security: What is it and How to Protect Your Pipelines

Vulnerability scans on Kubernetes with Pipeline

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub
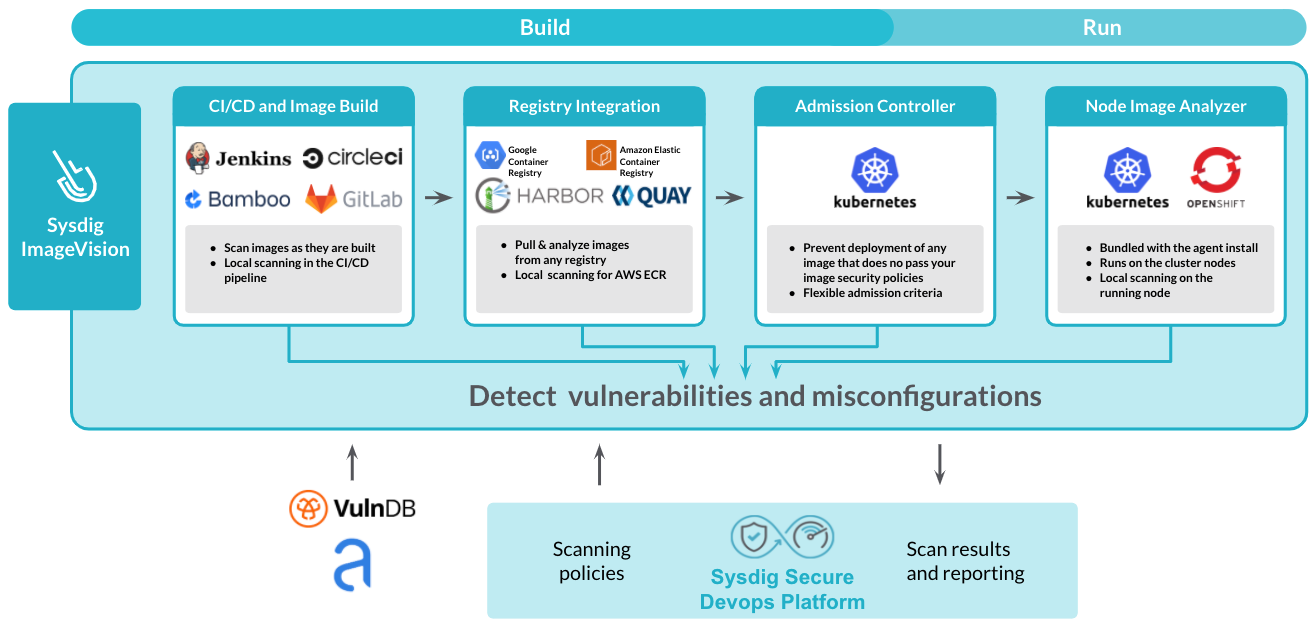
Image Scanning Overview :: Secure DevOps with AWS & Sysdig

The different stages of a CI/CD pipeline with the emphasis on parallel
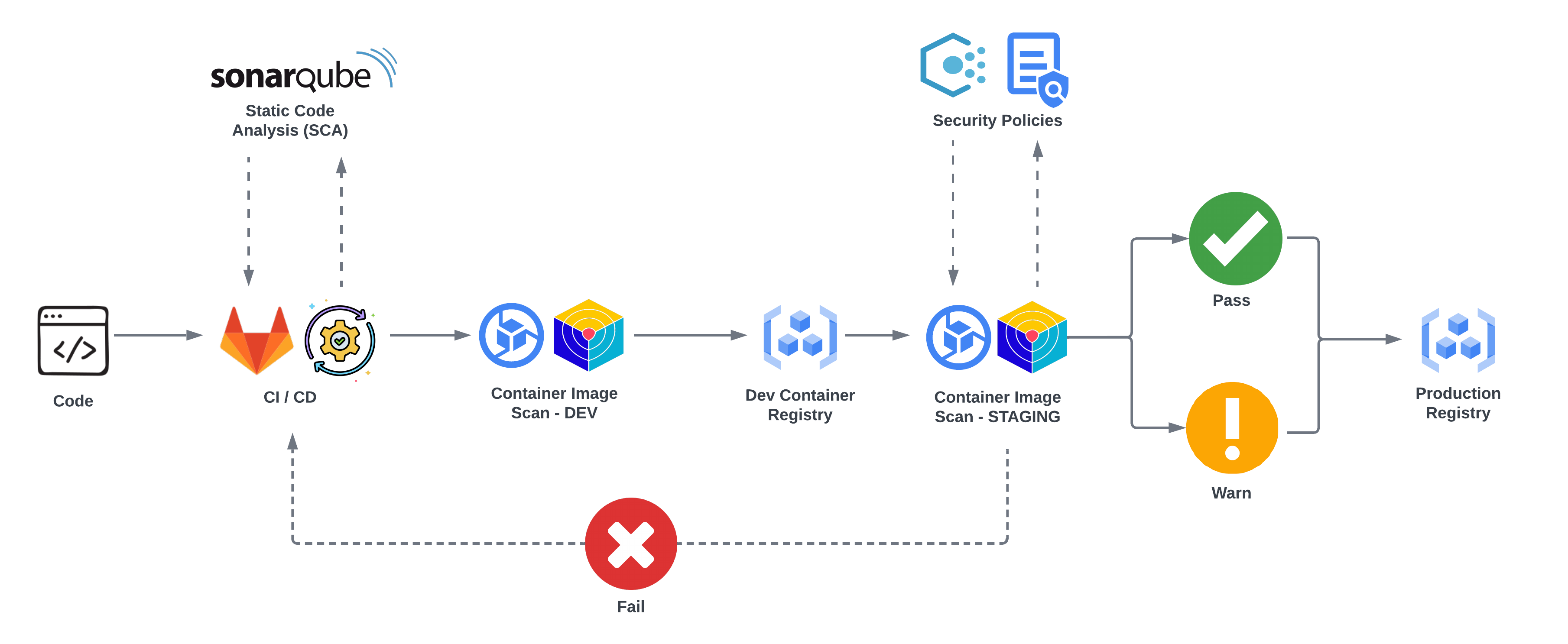
Adroit Cloud Consulting
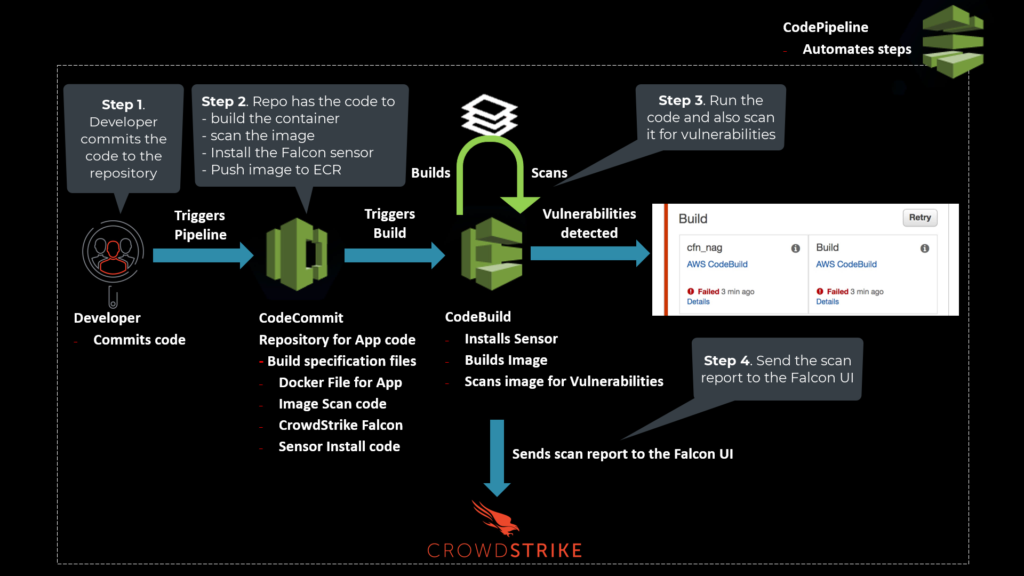
Shifting Left with the CrowdStrike and AWS CI/CD Pipeline

Checkov enables developer-first CI/CD security with new supply chain security policies - Bridgecrew Blog
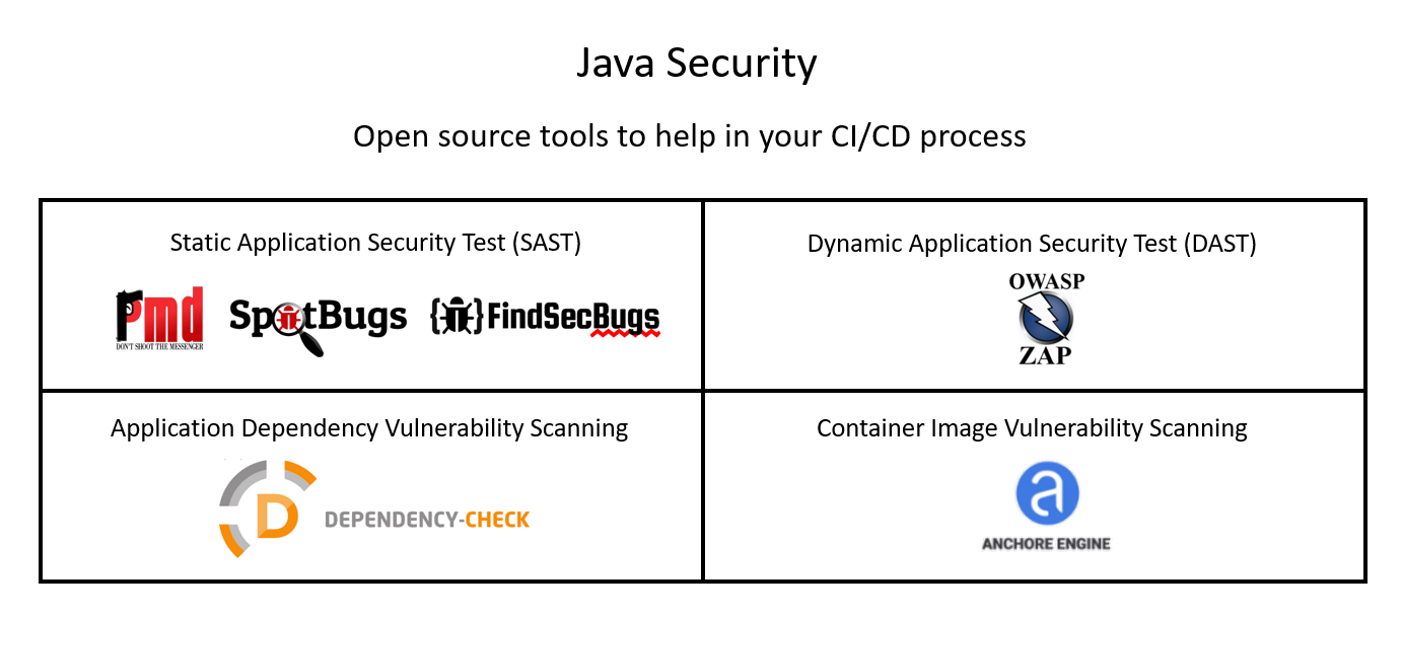
Java Security: Open Source tools for use in CI/CD pipelines