Cybercriminals are shapeshifting to evade security controls
Por um escritor misterioso
Descrição

Evil Corp Impersonates PayloadBin Group to Avoid Federal Sanctions

GenAI Cybersecurity: Where are we? Threats, Risks, and More
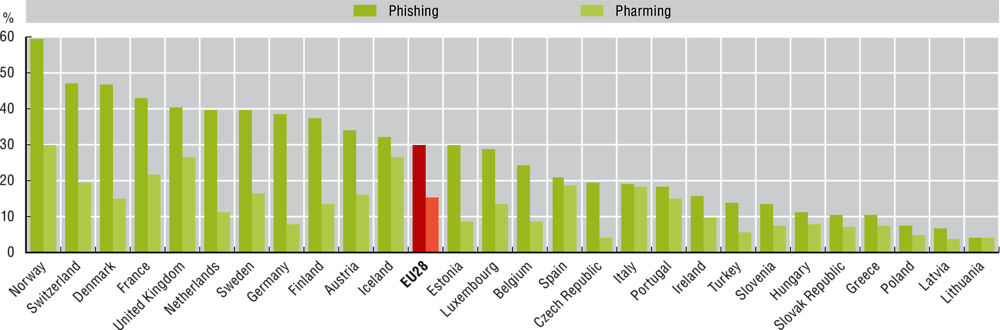
Chapter 7. Digital security, OECD Digital Economy Outlook 2020

Clipper Malware: What Is It and How Does It Impact Android Users?

The Top 23 Security Predictions for 2023 (Part 1)

Security - Page 15 of 48 - Tech Wire Asia

Cyble — Aurora – A Stealer Using Shapeshifting Tactics
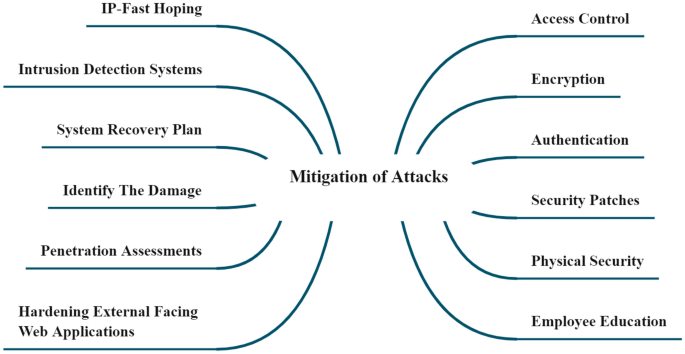
A survey on internet of energy security: related fields, challenges, threats and emerging technologies

3 Basic Security Practices Will Protect Your DNS From Compromise IT Infrastructure Advice, Discussion, Community - Network Computing

Microsoft Teams Phishing Used By Ransomware Access Broker

Personal Cybersecurity

GenAI Cybersecurity: Where are we? Threats, Risks, and More

Prevent Cyber Attacks: 10 Methods to Shield Your Digital Assets

Your company phone may be more at risk of a cybersecurity breach thanks to WFH