Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Why API attacks are increasing and how to avoid them

What is a fileless attack? How hackers invade systems without
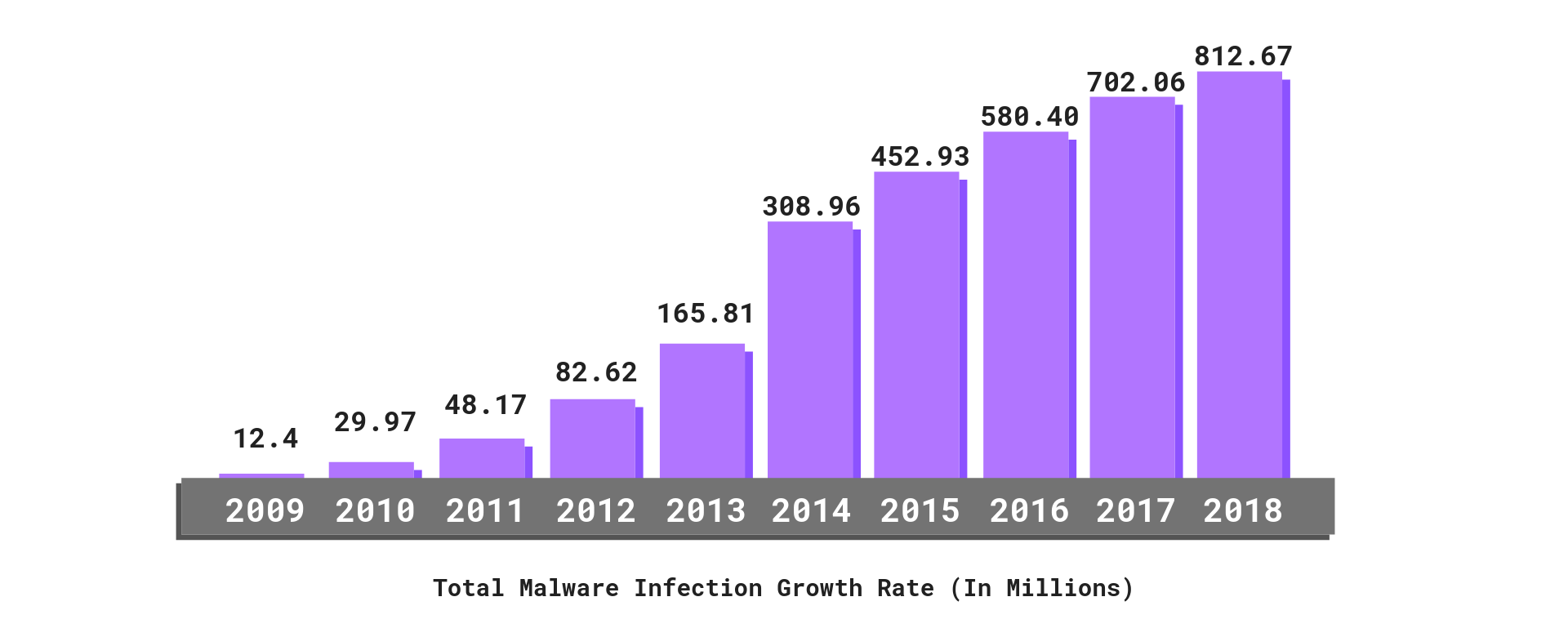
2023 Cyber Security Statistics: The Ultimate List Of Stats, Data

Privilege Escalation Attack and Defense Explained

FUD Malware obfuscation engine BatCloak continues to evolve

The Growing Threat of Fileless Attacks: Insights on Cybersecurity

How Hackers Rob Banks, 2018-05-21

Exploring Prompt Injection Attacks
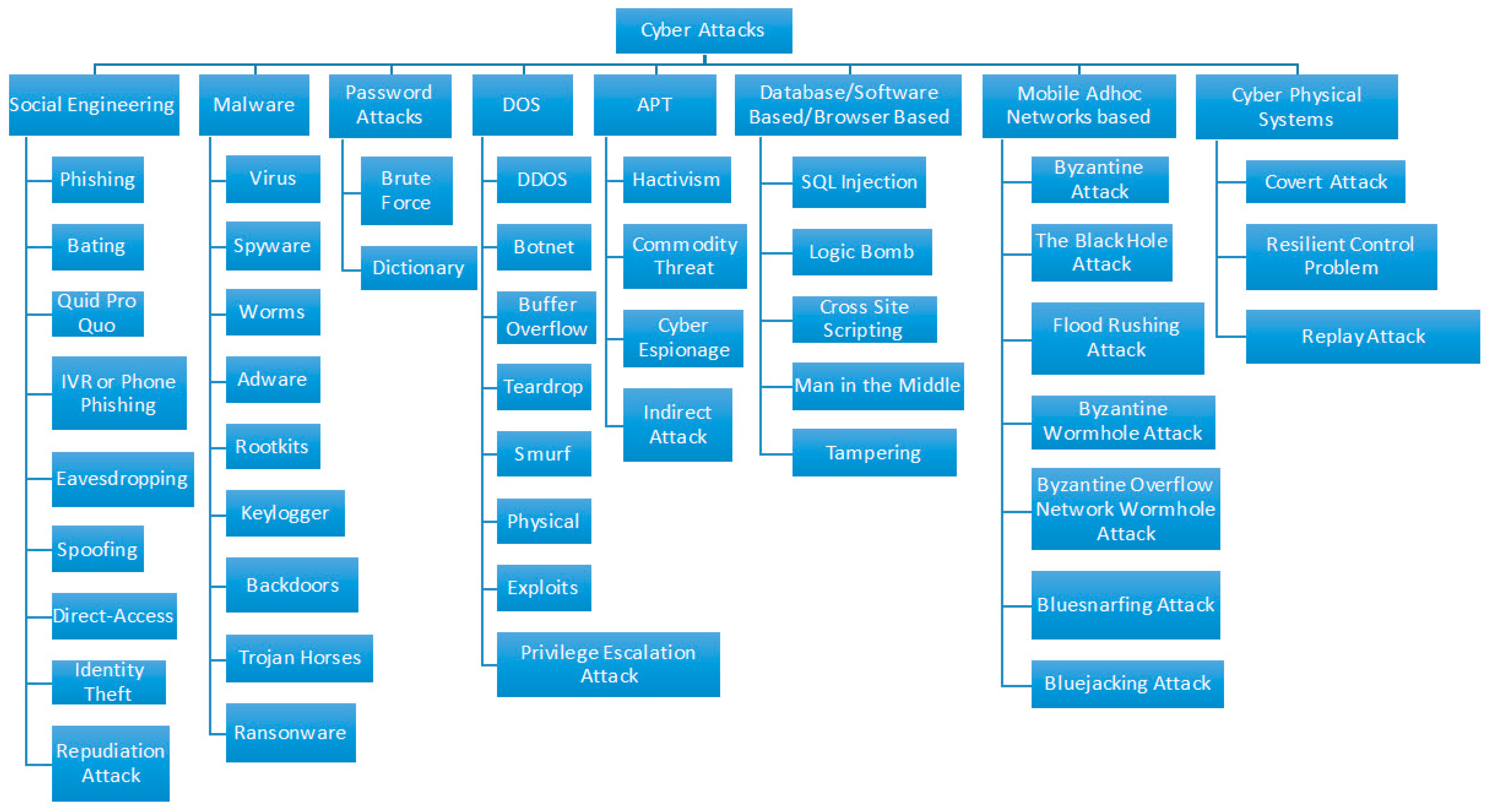
JCP, Free Full-Text

Denial-of-service attack - Wikipedia

How Hackers Use Social Engineering to Spread Dridex Malware
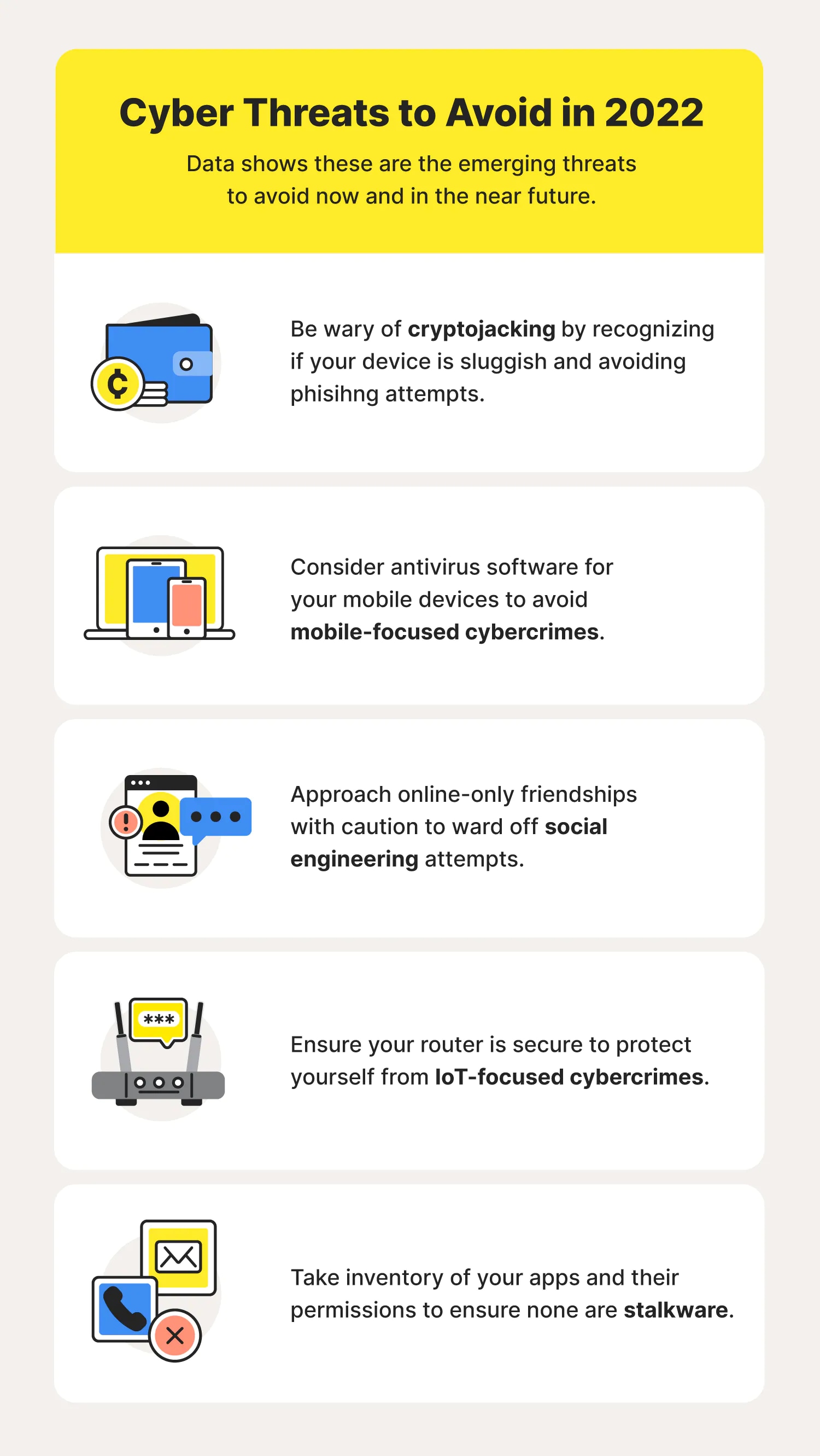
115 cybersecurity statistics + trends to know in 2024

The 16 Types of Malware and Cyber Attacks - SecureOps

Why Is Cybersecurity Important? 10 Challenges In 2022 - Trio