Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Descrição
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

30 Docker images downloaded 20M times in cryptojacking attacks
/images/2022/12/14/what_is_cryptojacking.jpg)
What Is Cryptojacking and How Does It Work?
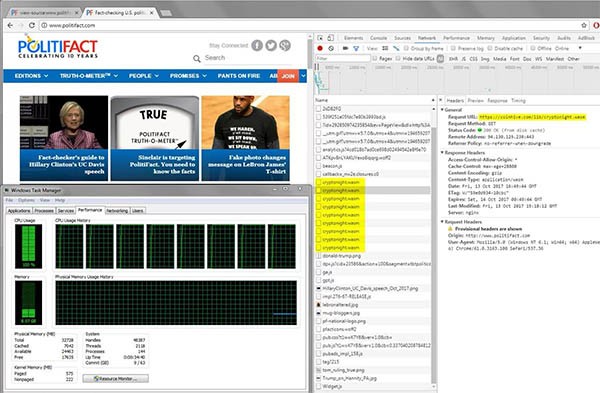
How Hackers Use Cryptojacking Malware to Take Over Computers to
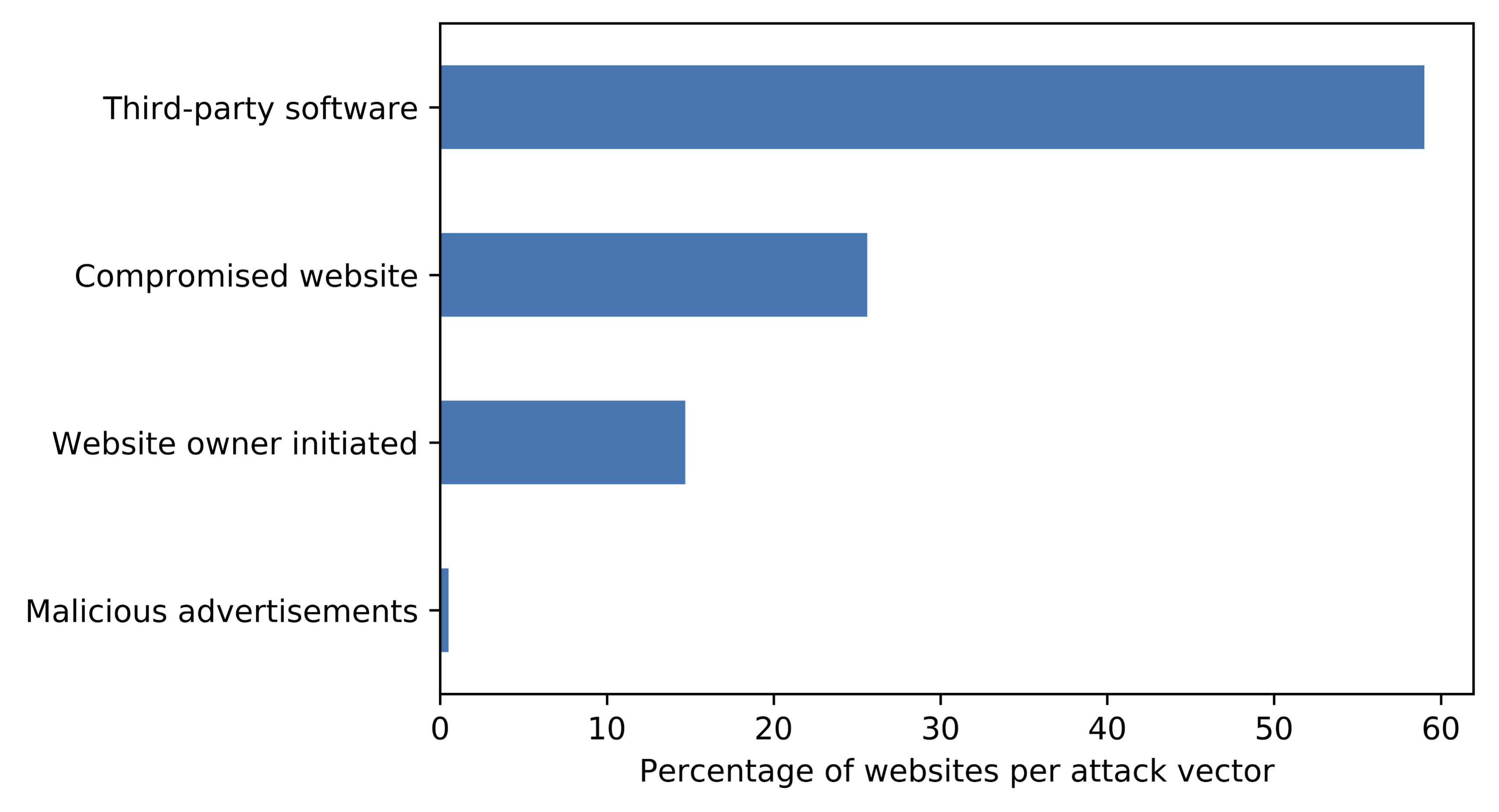
Blog: Infected third-party software key driver for cryptojacking

Cryptojacking (@cryptojacking) / X

PacNOG 23: Introduction to Crypto Jacking
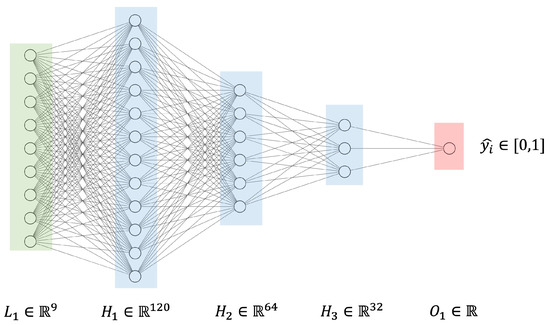
Applied Sciences, Free Full-Text

PDF) Browser Extension for Cryptojacking Malware Detection and

Reinforcing Financial Cybersecurity in the Eurozone by The

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs
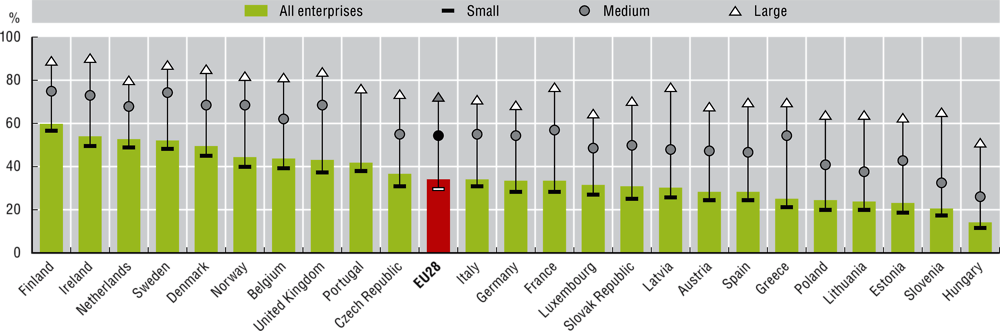
Chapter 7. Digital security OECD Digital Economy Outlook 2020

What is Cryptojacking? Detection and Preventions Techniques

ENISA's Threat Landscape and the Effect of Ransomware

PDF) Detecting Cryptojacking Web Threats: An Approach with