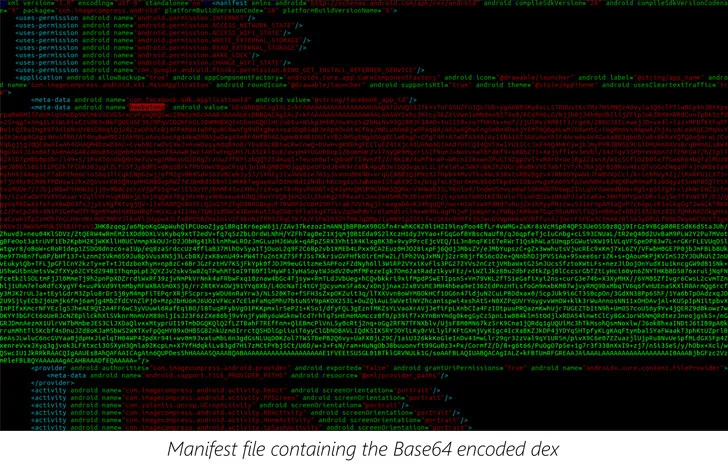
Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
Bypass malware detection in Google Play Store with Dynamic Code

Technical Advisory – New York State Excelsior Pass Vaccine

One million Android users hacked by 'most sophisticated' attack
Google Play threat market: overview of dark web offers

The many lives of BlackCat ransomware
SharkBot: a “new” generation Android banking Trojan being
TIB AV-Portal

Analysis of dynamic code updating in Android with security

Prevent Reverse Engineering (RE) of your Android application
Unofficial Telegram App Secretly Loads Infinite Malicious Sites
Joker Malware Apps Once Again Bypass Google's Security to Spread

Dynamic analysis and tampering