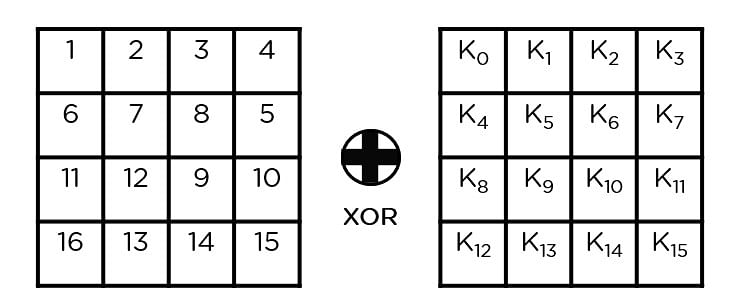
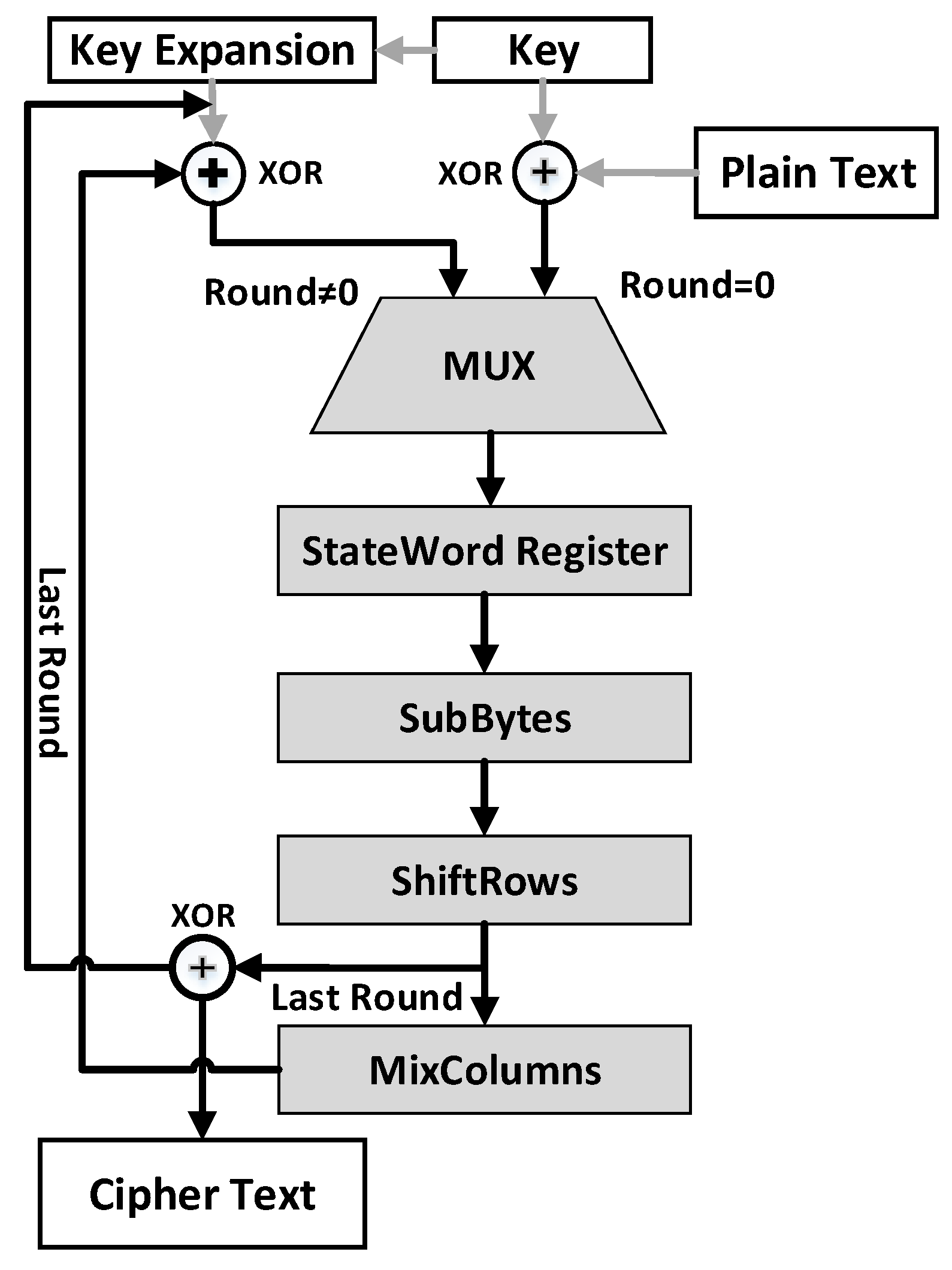
a Round operations and b key schedule of AES-128 algorithm. Each square
Por um escritor misterioso
Descrição

Building AES-128 from the ground up with python, by Henrique Marcomini, Sinch Blog

Virtex 7 FPGA Implementation of 256 Bit Key AES Algorithm with Key Schedule and Sub Bytes Block Optimization
Maximizing Security with AES Encryption: A Comprehensive Guide - CyberTalents

Figure 1 from Combined Attacks on the AES Key Schedule
What Is AES Encryption and How Does It Work? - Simplilearn
Applied Sciences, Free Full-Text
Sensors, Free Full-Text

PDF] Implementing AES Encryption on Programmable Switches via Scrambled Lookup Tables
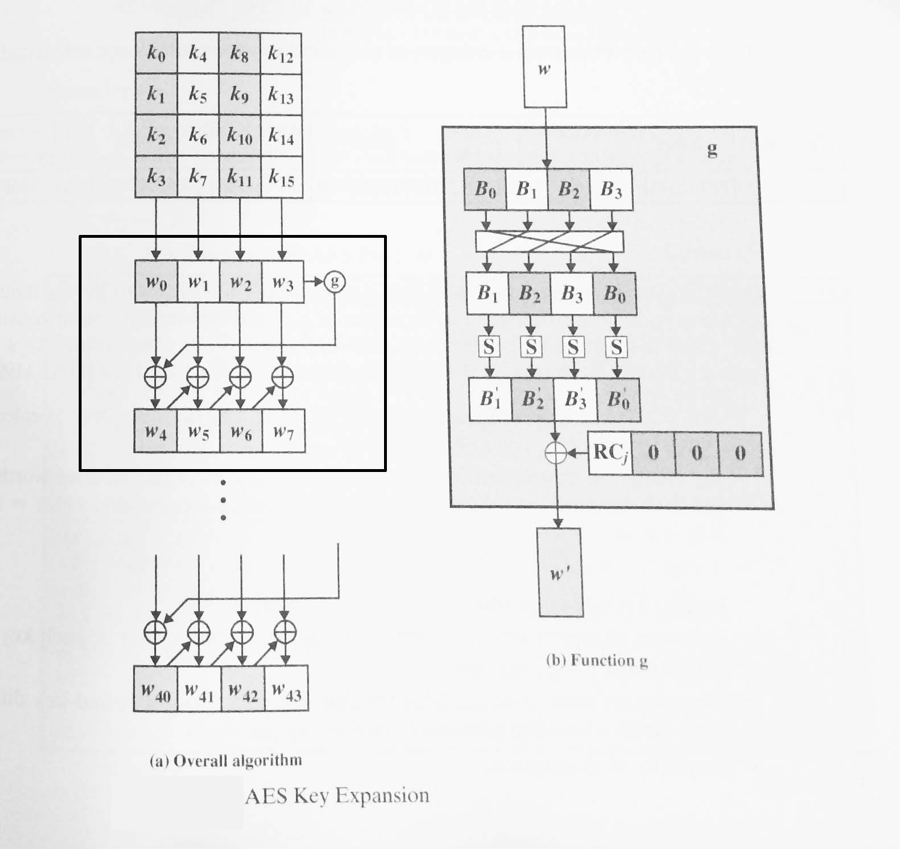
3.) Show the first eight words of the key expansion
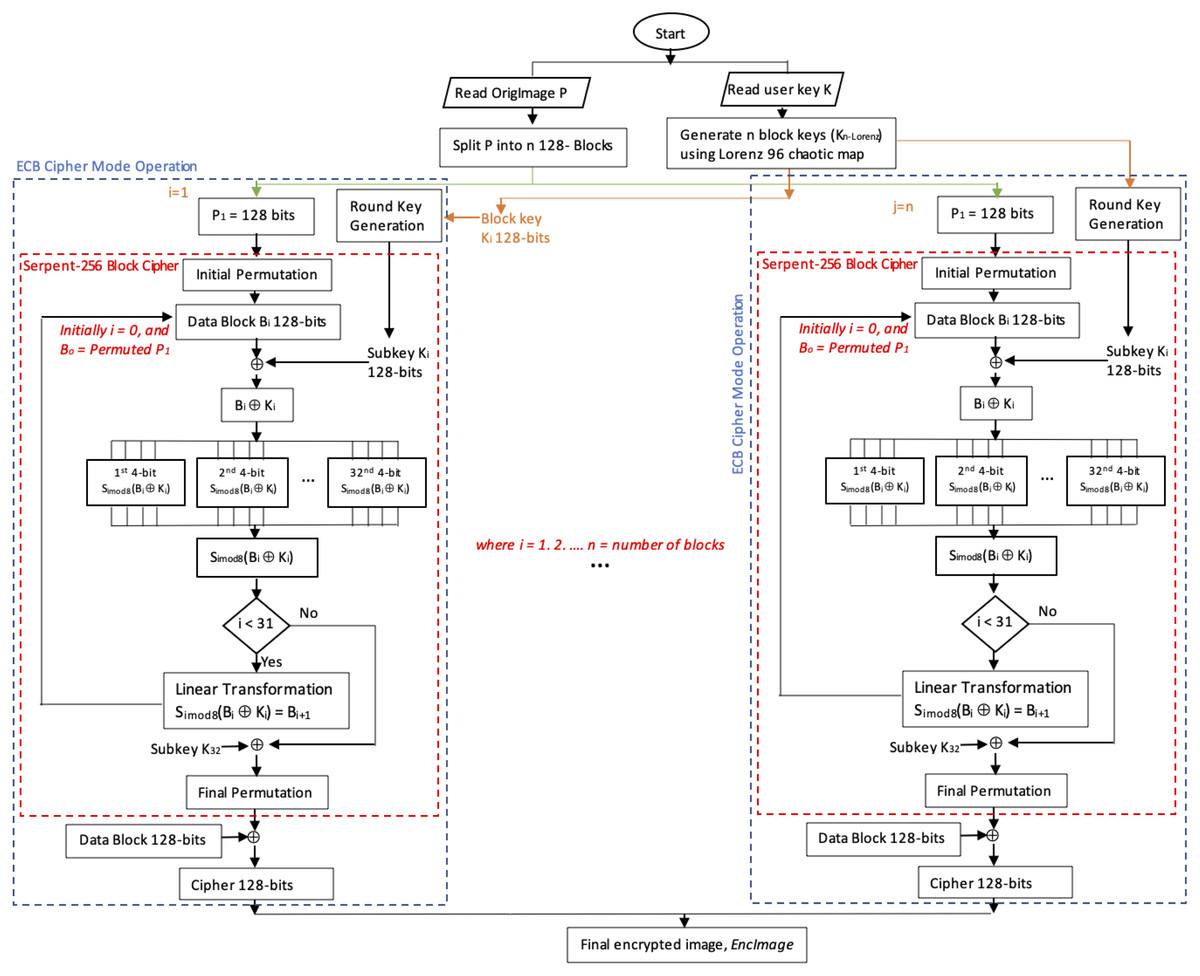
Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key generation and parallel computing for RGB image encryption [PeerJ]

Day-06 Quantum Cryptography — Advanced Encryption Standard(AES) Protocol, by Ajeet Kumar Bhardwaj @Applied mathematics

a Round operations and b key schedule of AES-128 algorithm. Each square

GitHub - m3y54m/aes-in-c: Basic implementation of AES in C + Tutorial