Windows Command-Line Obfuscation
Por um escritor misterioso
Descrição
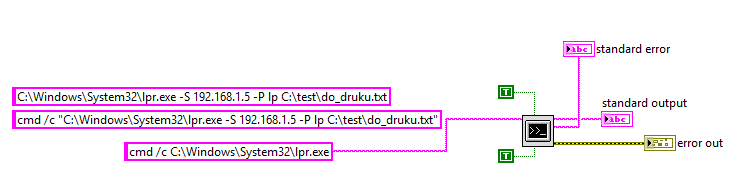
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.

Obfuscated Command Line Detection Using Machine Learning - REAL
Florian Roth on X: Sigma rule to detect suspicious Unicode
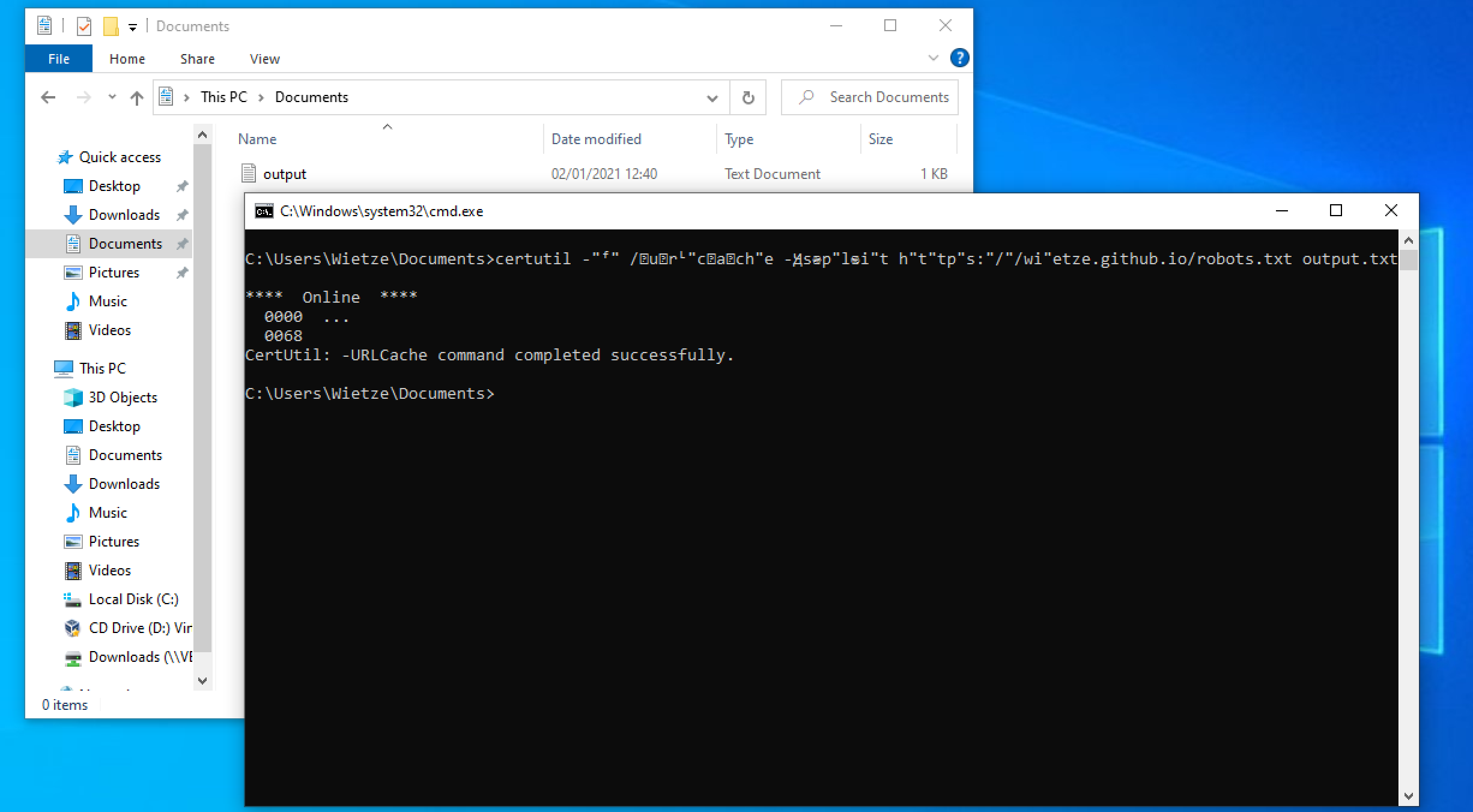
Windows Command-Line Obfuscation
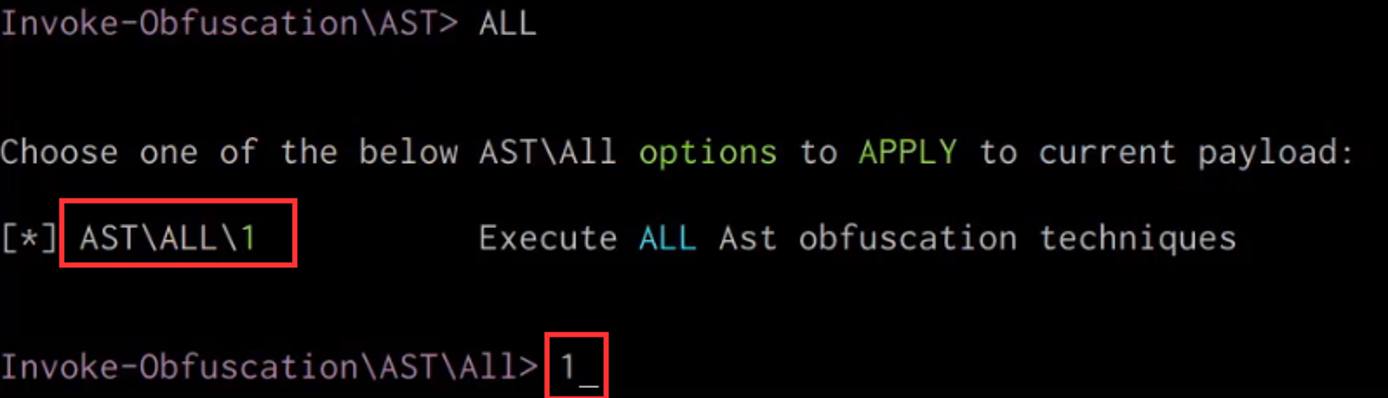
Windows Red Team Defense Evasion Techniques
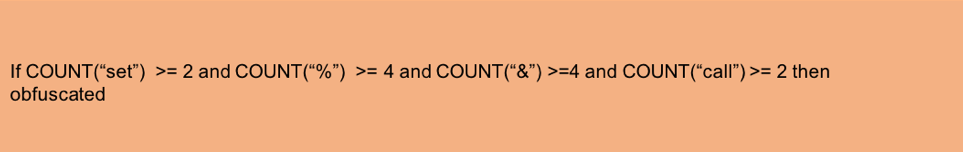
Obfuscated Command Line Detection Using Machine Learning

Invoke-Obfuscation – Liam Cleary [MVP Alumni and MCT]

Commandline Obfusaction - Red Team Notes
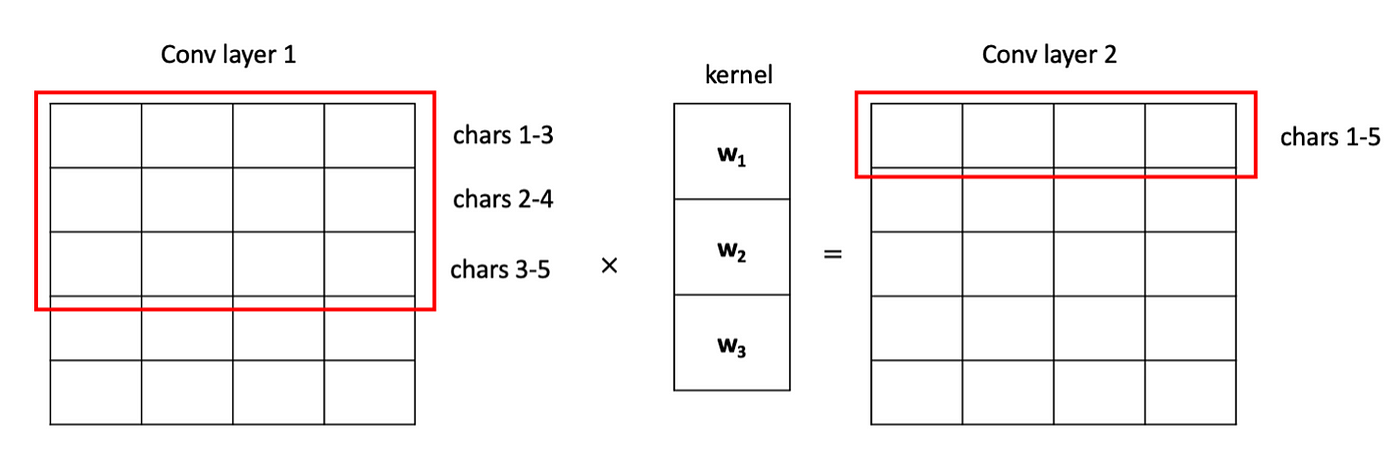
Using Deep Learning to Better Detect Command Obfuscation

Commandline Obfusaction - Red Team Notes

Command Line Interface — Dotfuscator Community User Guide 6.3

Practical Behavioral Profiling of PowerShell Scripts through
Dosfuscation in the wild

Commandline Obfusaction - Red Team Notes

Invoke-Obfuscation – Liam Cleary [MVP Alumni and MCT]
Cmd and Conquer: De-DOSfuscation with flare-qdb