Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Descrição
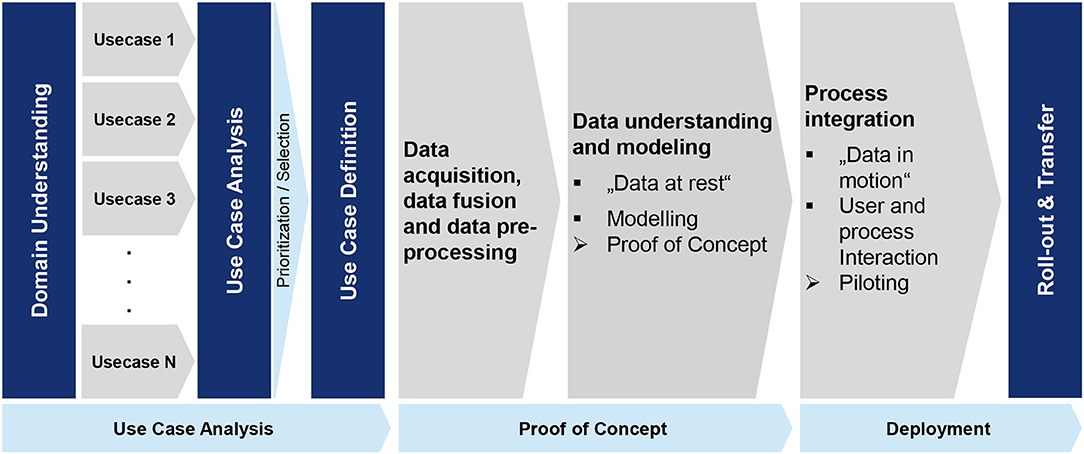
Frontiers Implementation and Transfer of Predictive Analytics for Smart Maintenance: A Case Study
How to adjust Trend Micro scan settings on Windows

Netskope Client Configuration - Netskope Knowledge Portal

Connected Philanthropy Podcast - Foundant Technologies
Common questions about Hosted Email Security
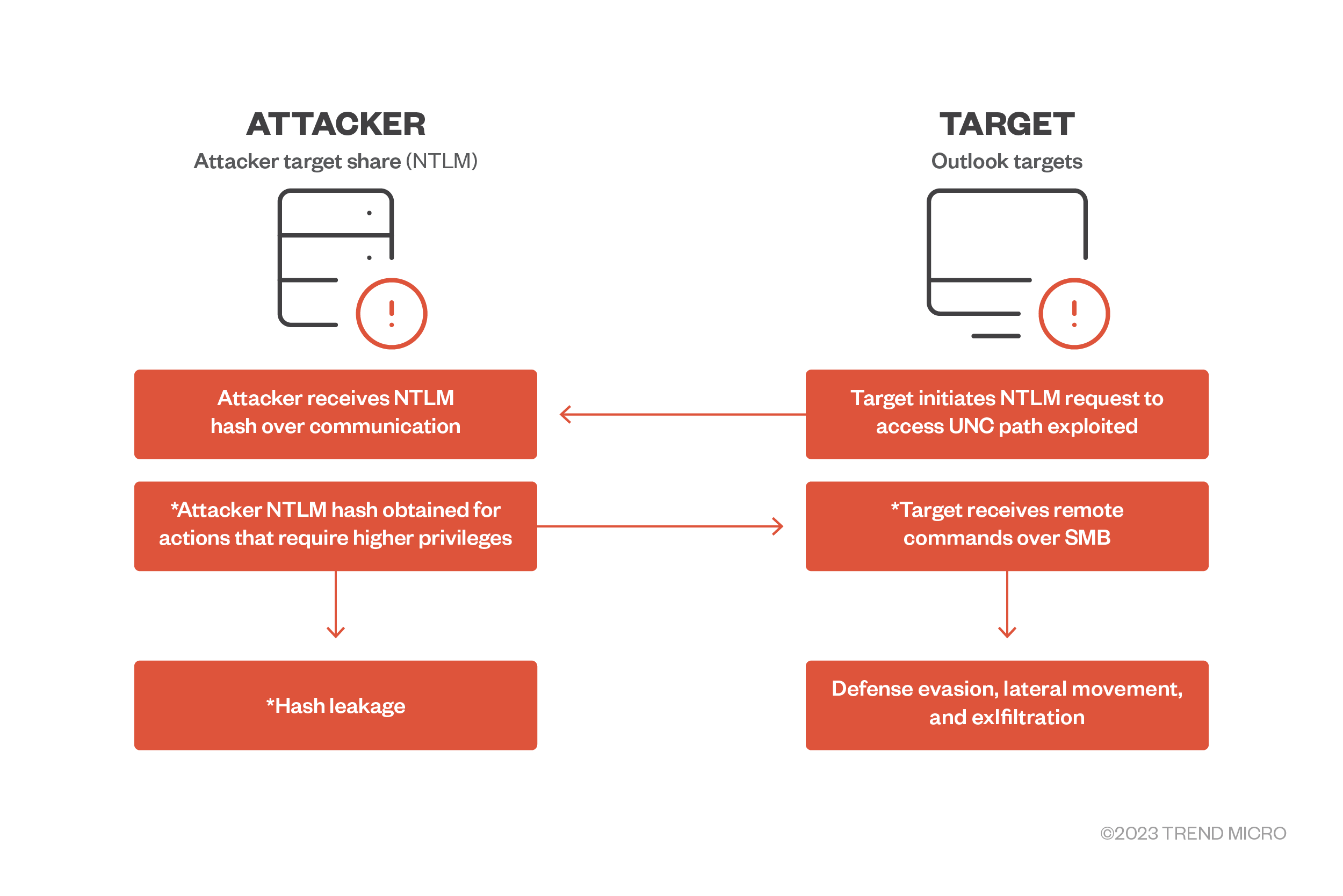
Patch CVE-2023-23397 Immediately: What You Need To Know and Do
Feature testing steps - OfficeScan XG

Trend Micro Antivirus+ Security Review
Passed a potential security risk' in Virus/Malware Logs

Wi-Fi Spoofing: A Major Threat to Network Security - Cloud RADIUS
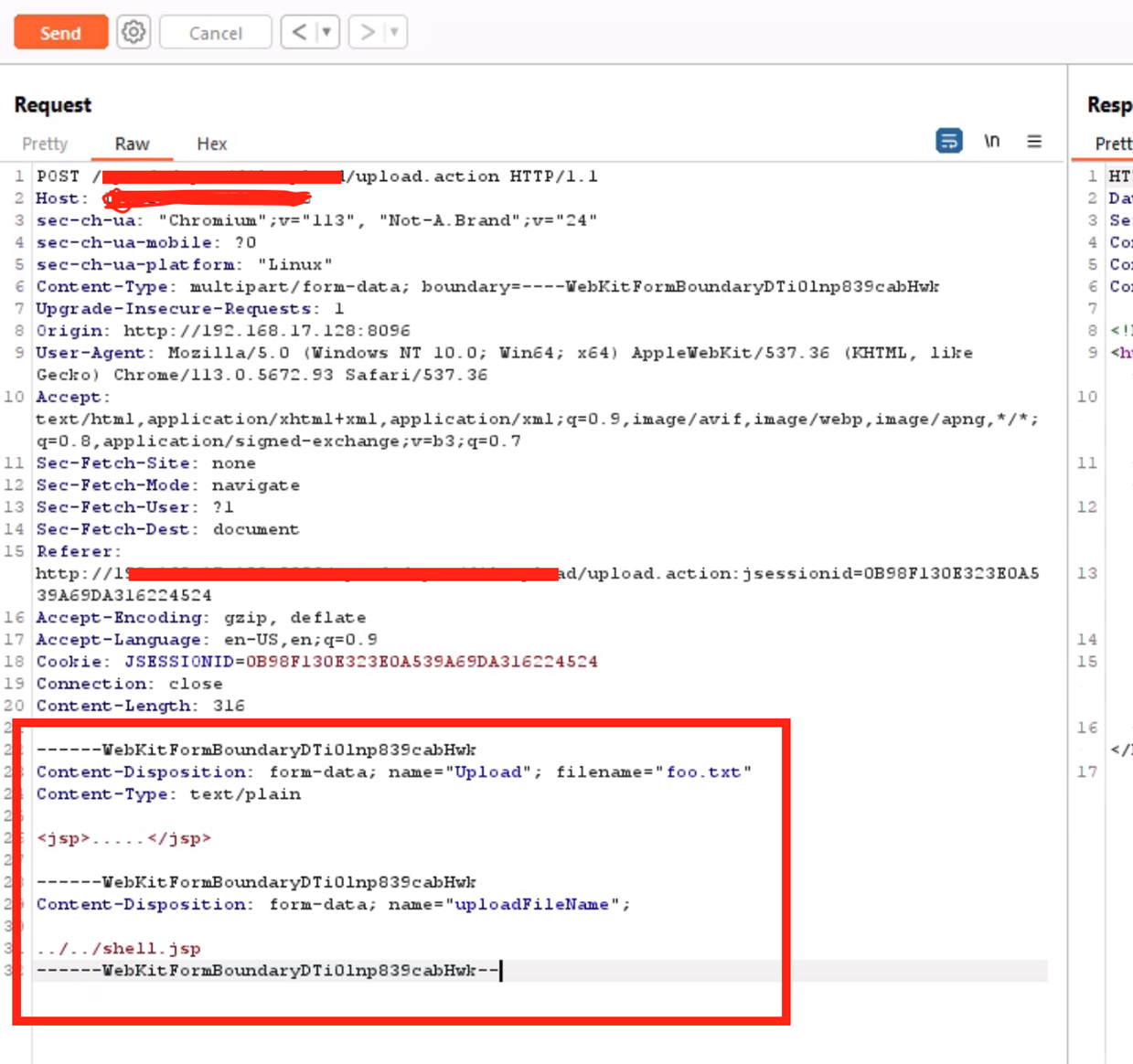
Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit







