Suspicious User Controls
Por um escritor misterioso
Descrição

Cyber Triage - Finding Suspicious Program Activity
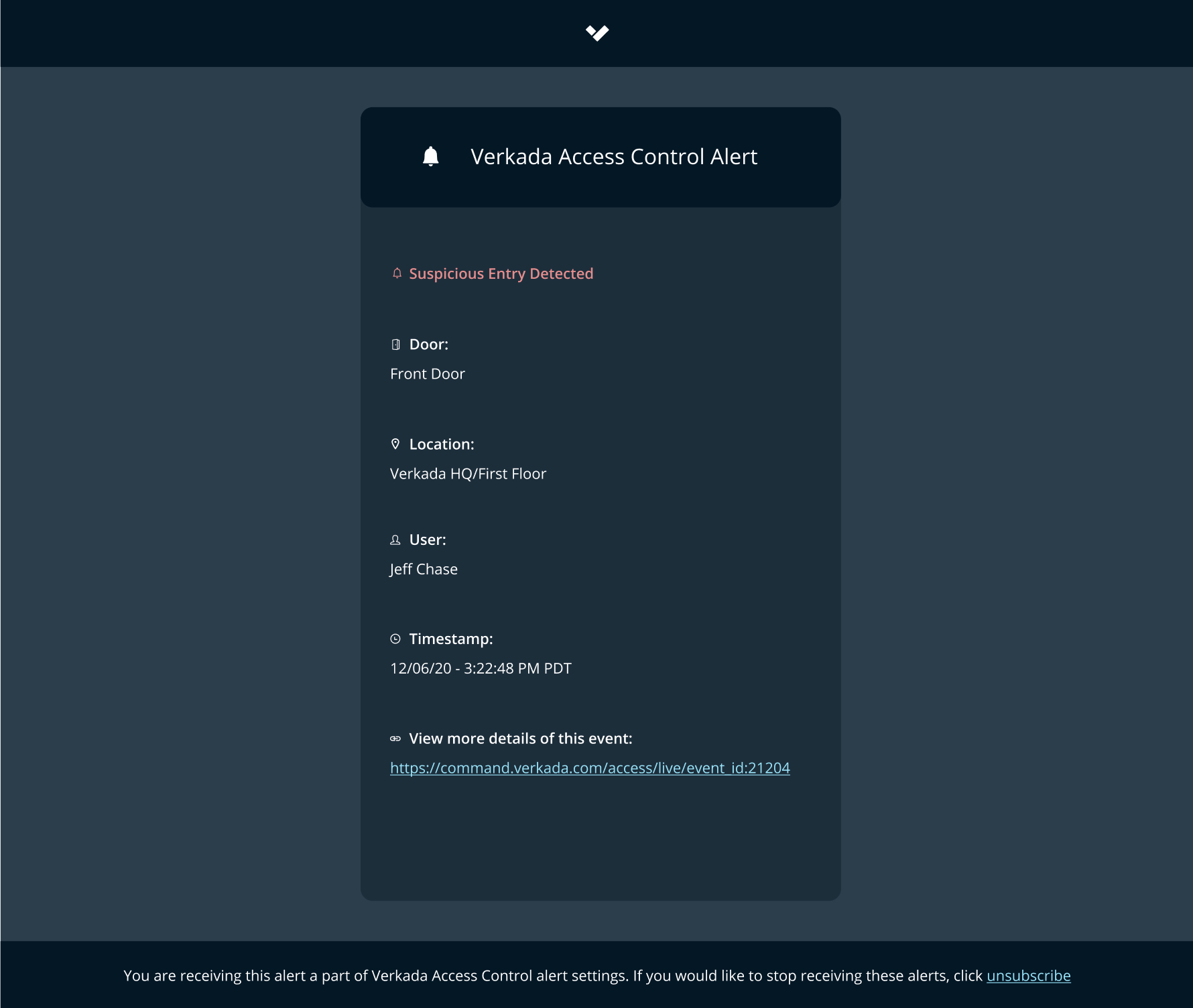
Stay Ahead of Critical Access Control Events With New Notifications
Tip 5: Search for related party transactions – MindBridge: English (US)

Zero trust element #4: Assess risk (adaptive control)
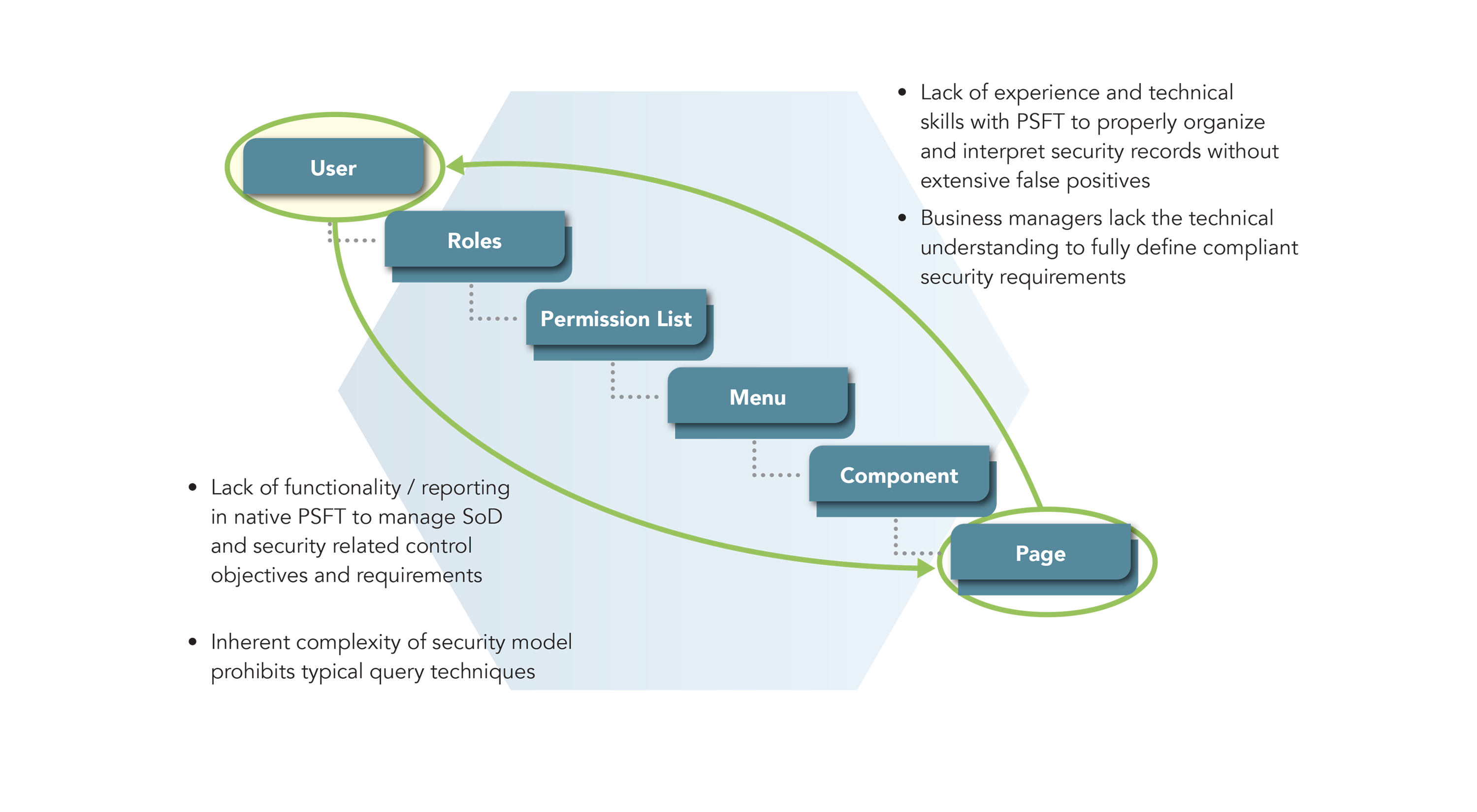
Segregation of Duties for PeopleSoft
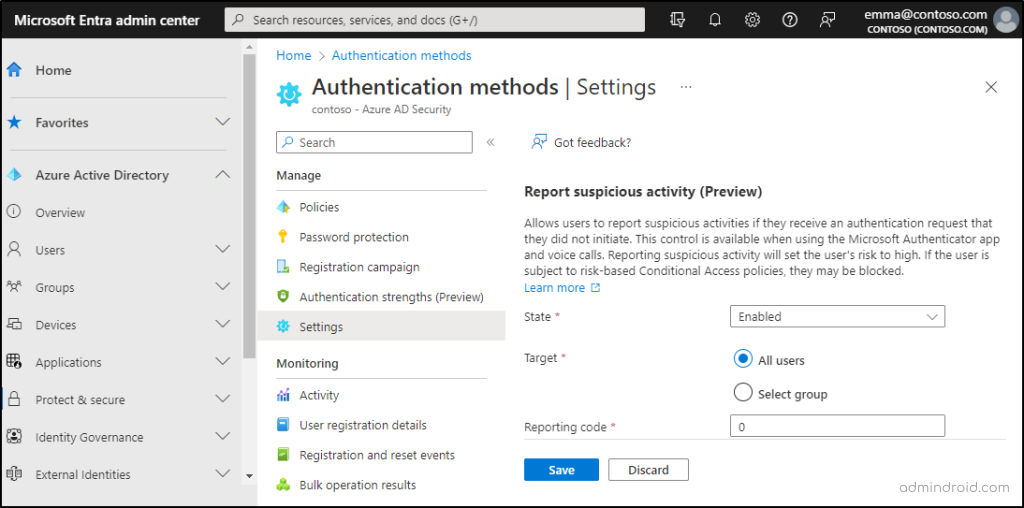
Enable Report Suspicious Activity in Azure AD to Stay Alerted on Suspicious MFA Requests
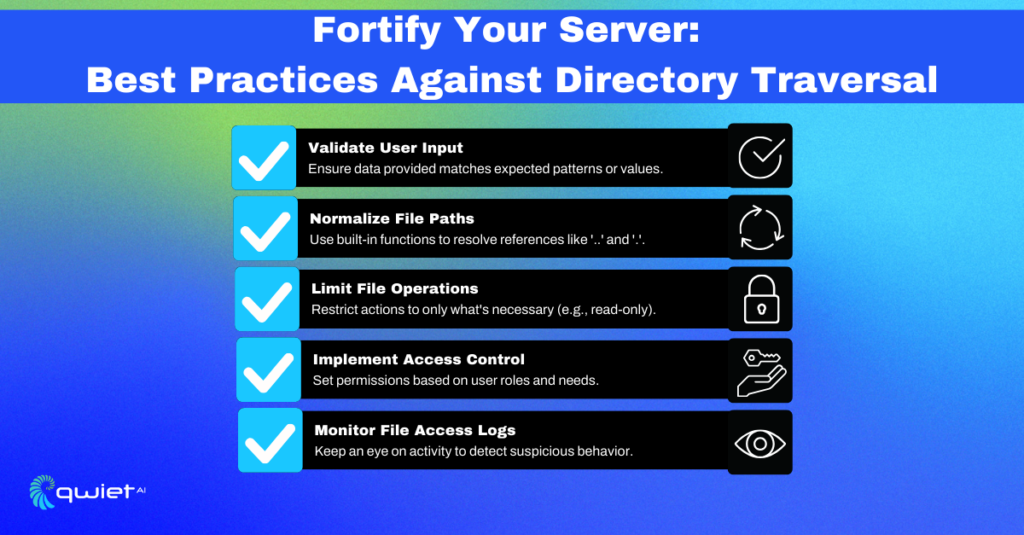
Preventing Directory Traversal Attacks: Best Practices for File Handling – Preventing the Unpreventable
User Activity Monitoring for Federal Agencies

Cloudlock K-12 Statement of Value





/i.s3.glbimg.com/v1/AUTH_da025474c0c44edd99332dddb09cabe8/internal_photos/bs/2023/h/s/JT4daSTLiiYzsBlSJFTQ/5g-games-divulgacao.jpg)