Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Descrição
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Unpacking Emotet Trojan. Emotet, in general, is a banking…, by mov eax, 27

What is Emotet Malware and How Do You Defend Against it?

What is Emotet How to best protect yourself
Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet
Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet

Dimitris Kolotouros (@kolotoor) / X

GIAC Reverse Engineering Malware (GREM) - Credly
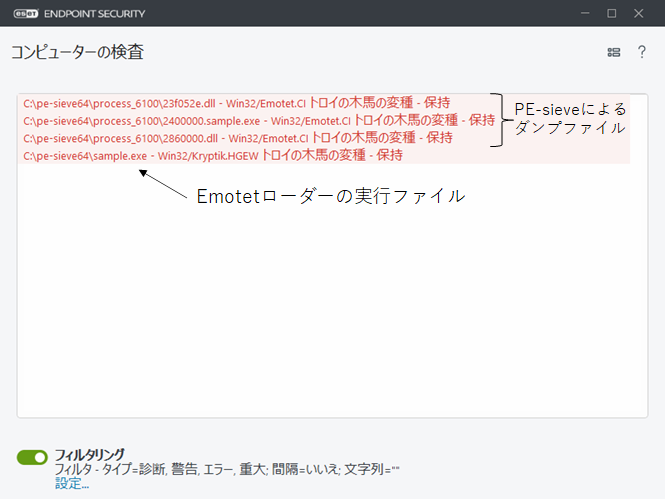
PE-sieve サイバーセキュリティ情報局
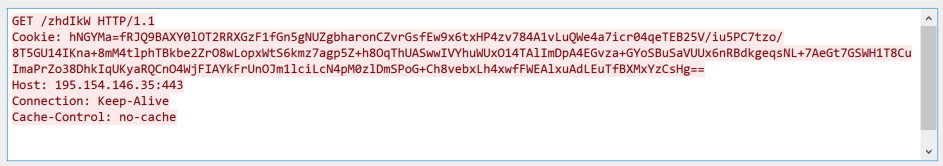
Return of Emotet: Malware Analysis
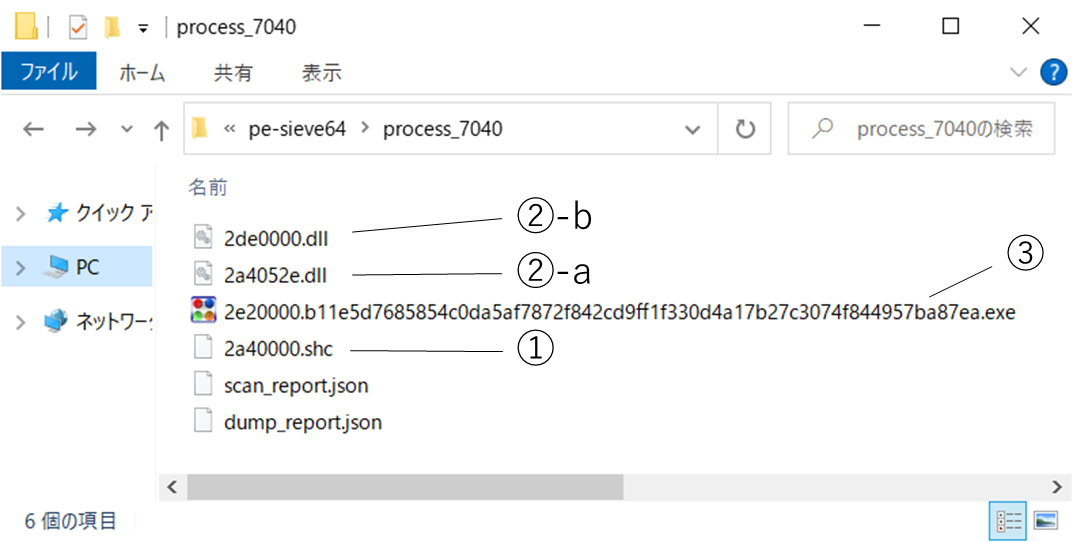
PE-sieve サイバーセキュリティ情報局
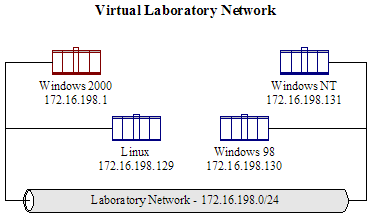
Methodology for Reverse-Engineering Malware