Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

TryHackMe Cyber Security Exercises and Labs

Dynamic malware analysis [34]

Malware Analysis: Protecting Your Network from Cyber Attacks
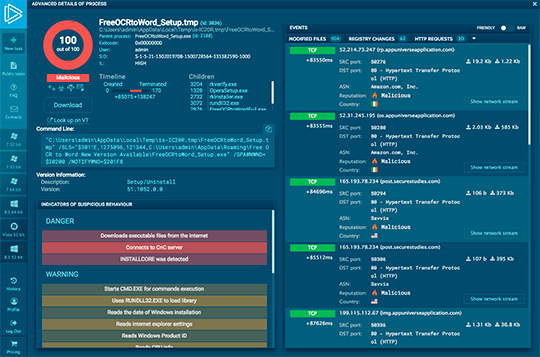
Interactive Online Malware Sandbox

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

What is Malware? Definition, Types, Prevention - TechTarget

How to Do Malware Analysis?

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Top 10 Types of Information Security Threats for IT Teams