Malware analysis Malicious activity
Por um escritor misterioso
Descrição
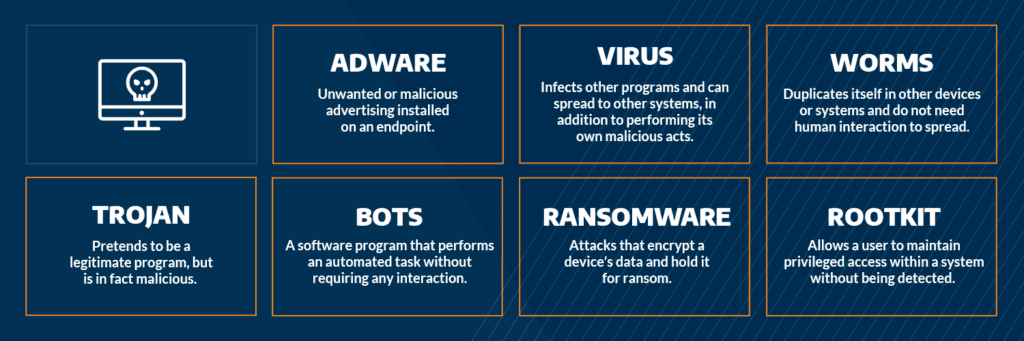
Most Common Malware Attacks

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware analysis file Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
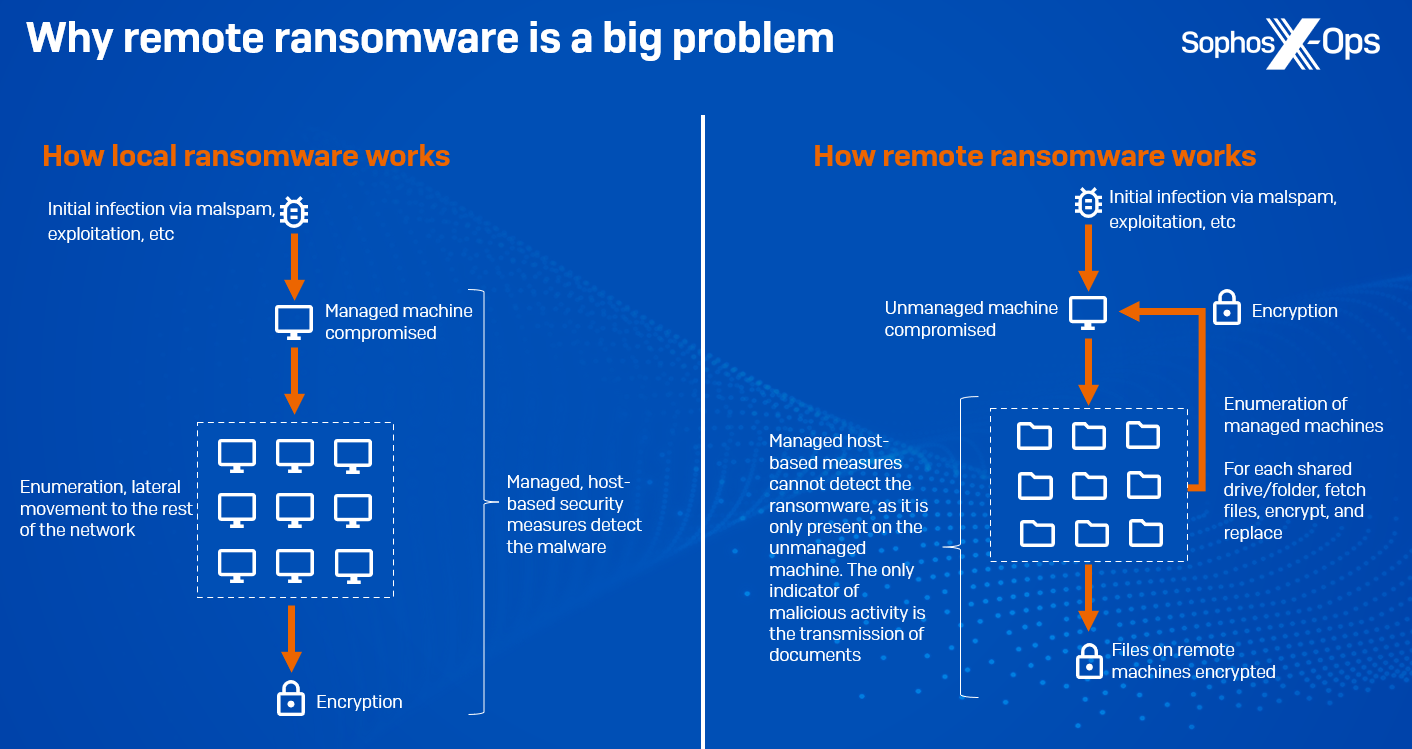
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

What to Include in a Malware Analysis Report

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable







