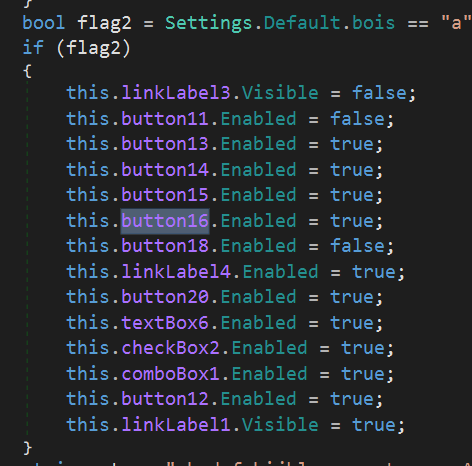
Malware analysis Malicious activity
Por um escritor misterioso
Descrição
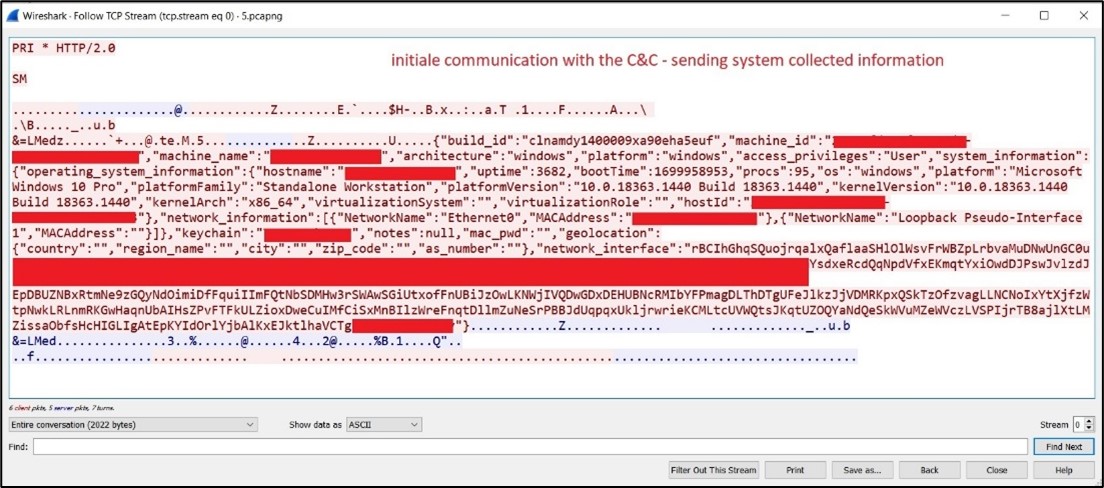
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Endpoint Detection and Response, Free - What is EDR Security?

AlienVault - Open Threat Exchange

A detailed analysis of the Menorah malware used by APT34

What is Malware? Definition, Types, Prevention - TechTarget

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

Malware analysis file Malicious activity
Lab 6-1 Solutions - Practical Malware Analysis [Book]

Malware Analysis - What is, Benefits & Types (Easily Explained)

StopRansomware: Rhysida Ransomware
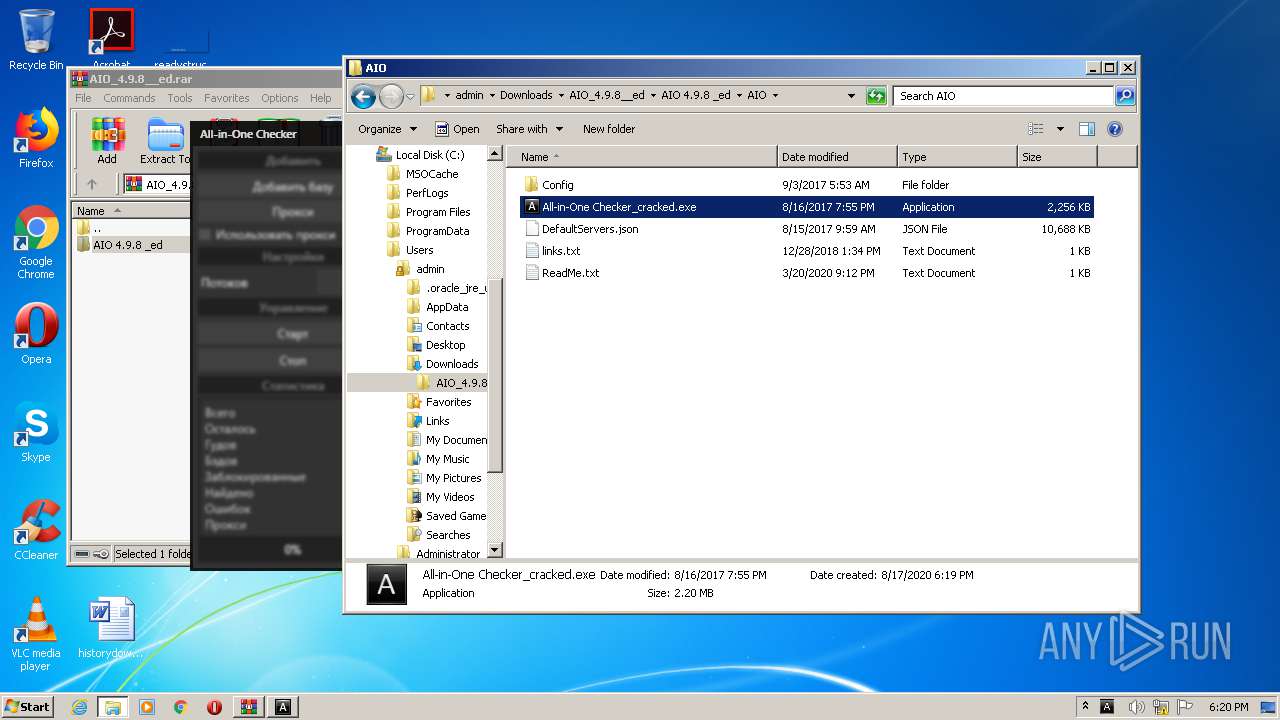
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog