Malware analysis Malicious activity
Por um escritor misterioso
Descrição

What to Include in a Malware Analysis Report

Malware analysis index.html Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
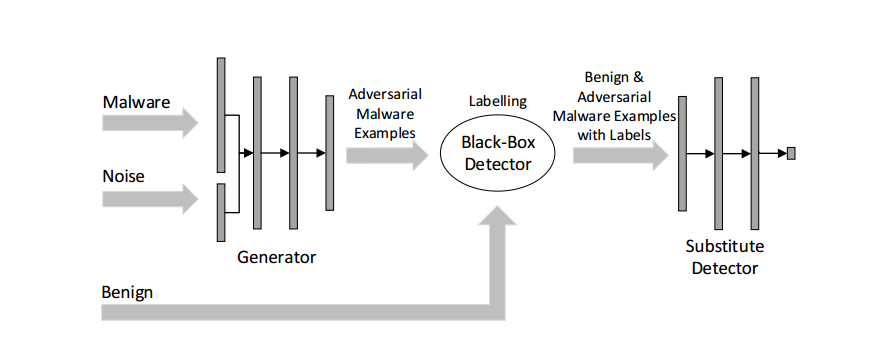
Malware Detection

Malware analysis mykey_.rar Malicious activity

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights
Malware analysis lockysample.bin.zip Malicious activity
Malware analysis Pixelus Deluxe.zip Malicious activity

AlienVault - Open Threat Exchange
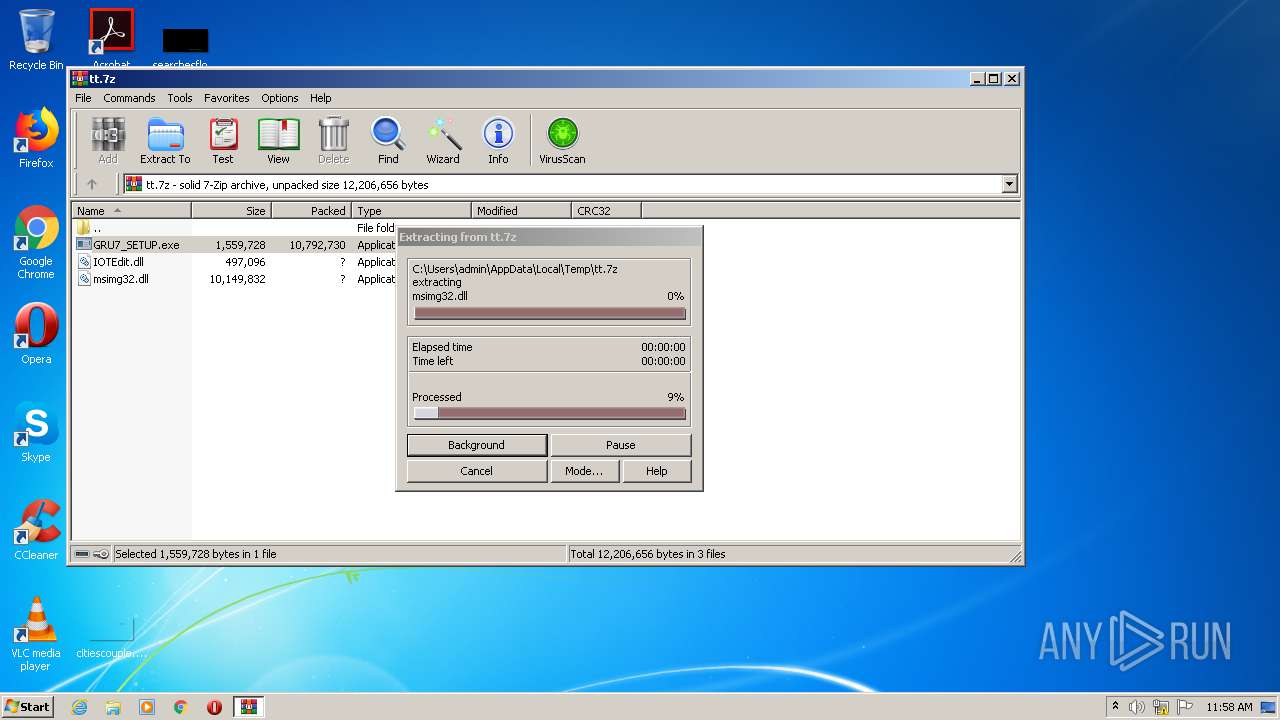
Malware analysis tt.7z Malicious activity

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

What is Malware? Definition, Types, Prevention - TechTarget

Malware Analysis: Protecting Your Network from Cyber Attacks

Malware Analysis: Steps & Examples - CrowdStrike