Hacker Simulator - Succeed 5 Phishings
Por um escritor misterioso
Descrição
scansystem and scanfolder have been replaced by the ls commandI edited out the time between contracts, the time it takes for them to respond on fishbook, and
AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)

DegerPhish - The phishing simulation by DegerTech - Simulate phishing attacks on your enterprise - DegerTech – Protect your company against phishing, hacker attacks & cyber crime – phishing awareness, pentesting, consulting

What.Hack: Engaging Anti-Phishing Training Through a Role-playing Phishing Simulation Game

Five Dangerous Phishing Scams
ThreatGEN: Red vs. Blue on Steam
Phishing Simulations
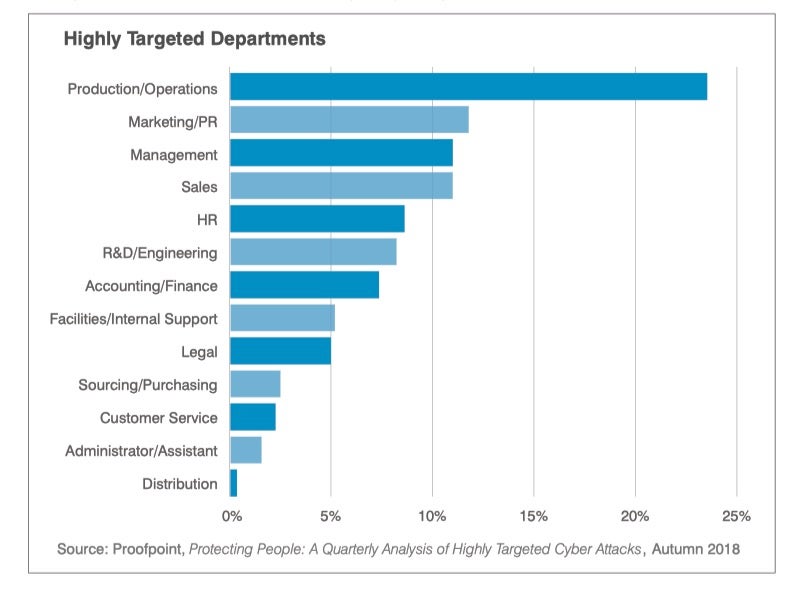
Targeted Phishing Revealing The Most Vulnerable Targets

5 Phishing Techniques Organizations in the MENA Region Should Be Aware of - Kratikal Blogs

19 Examples of Common Phishing Emails

What is Phishing Simulation? Benefits & How it Works

Announcing the Public Preview of Attack Simulator for Office 365 Threat Intelligence - Microsoft Community Hub

Phishing Arctic Wolf
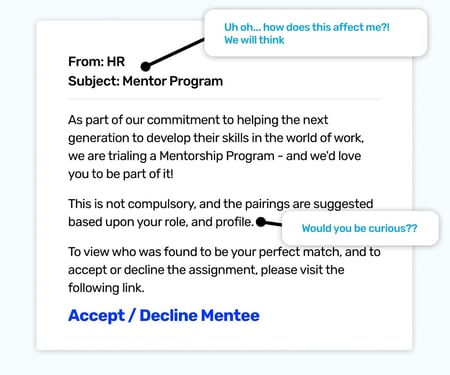
Top 5 Must-Know Phishing Simulation Templates - April Edition