Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Descrição
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

Using an Interactive Cross-site Scripting Backdoor

Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure
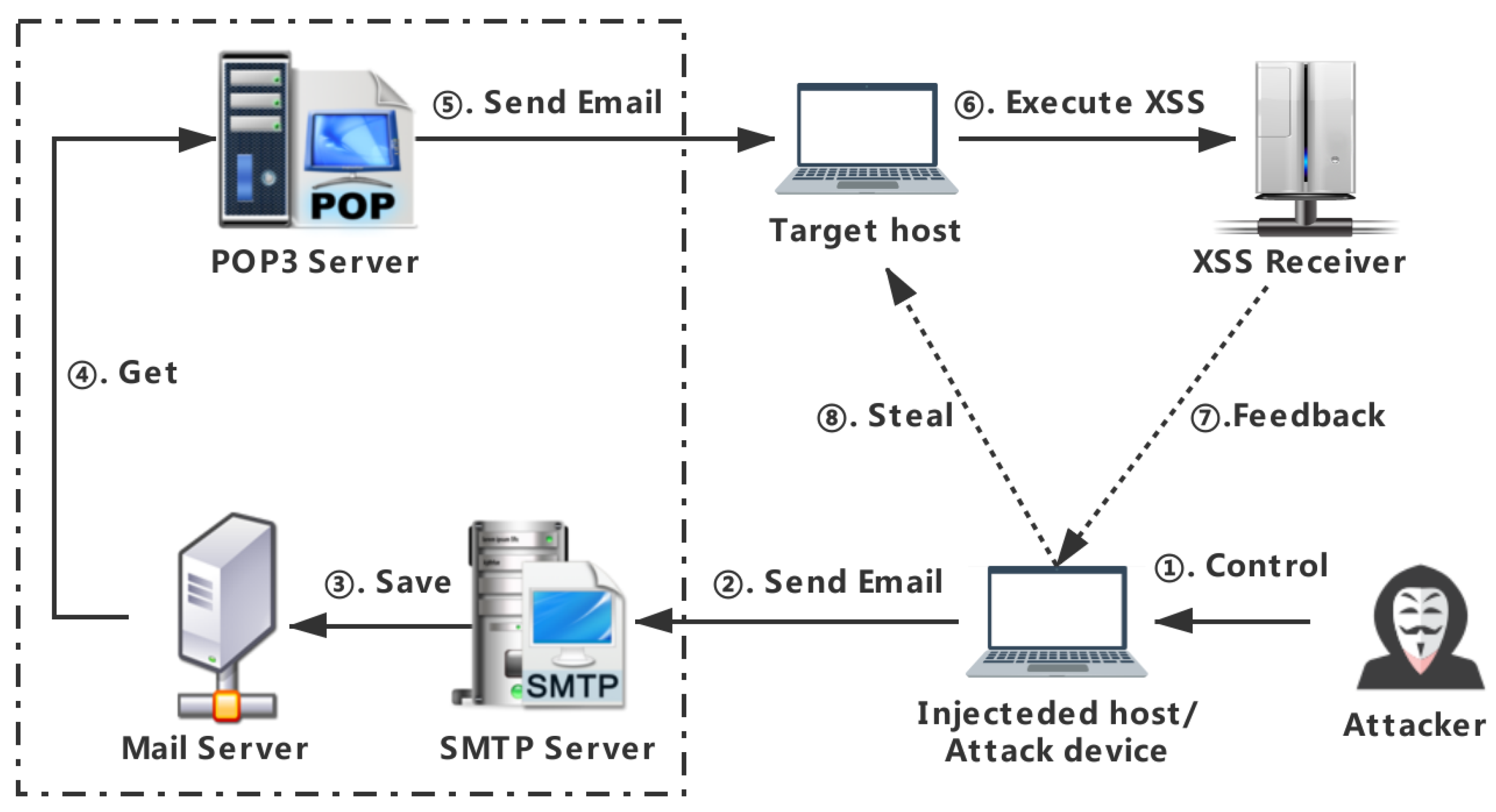
Applied Sciences, Free Full-Text
What are some ways of protecting against cross-site scripting (XSS) injection through cookies? - Quora
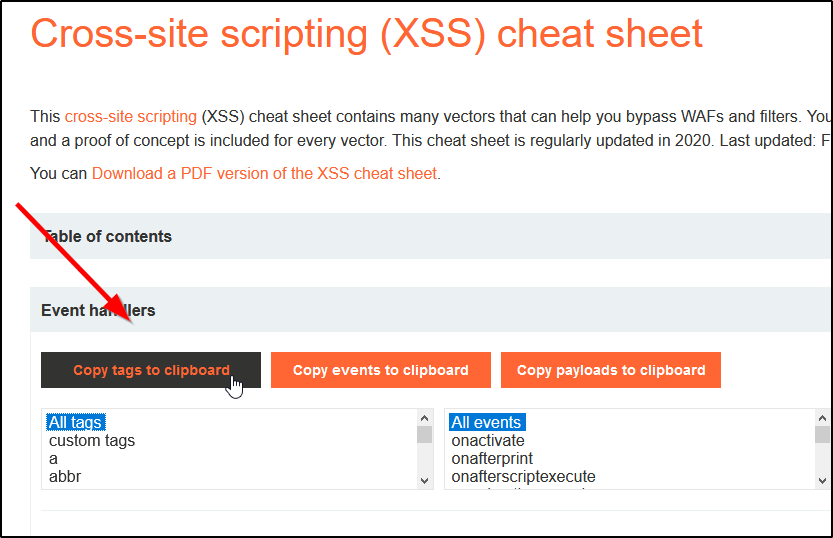
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
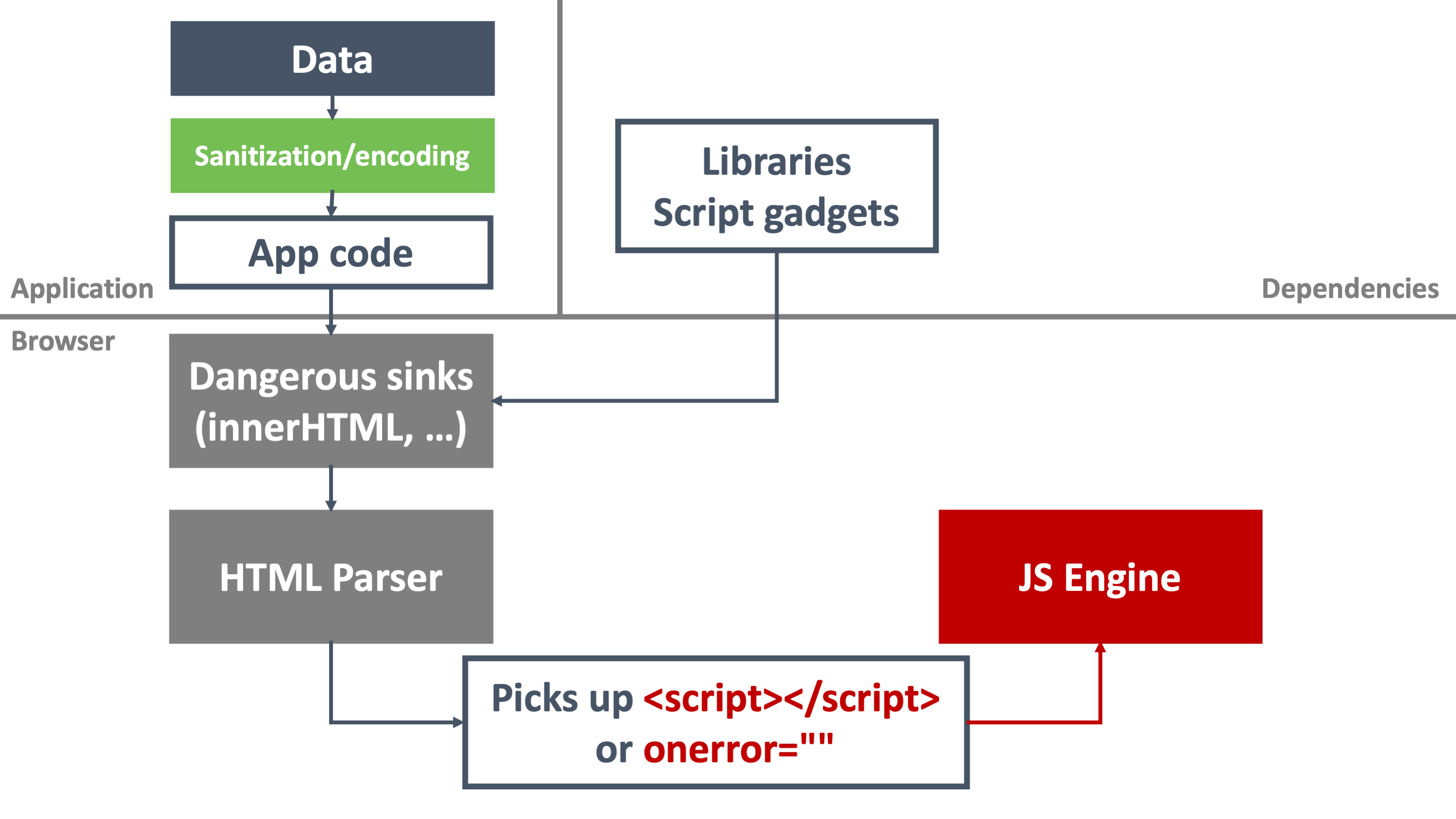
Securing SPAs with Trusted Types

Mitigate cross-site scripting (XSS) with a strict Content Security Policy (CSP), Articles
Encoding and escaping untrusted data to prevent injection attacks - The GitHub Blog

How to Find XSS Vulnerability: A Step-by-Step Guide & Tools